VoIP services – How does it work?
The world over, communication – reliable and secure – is taking on a more critical role in the functioning of organizations and businesses. The more geographically spread your organization is, the more important it becomes to keep communication networks up and running.
Voice Over Internet Protocol (VoIP) has gained tremendous traction over the last decade and has become a popular choice for organizations looking for cost-effective and reliable communication networks to manage their growing business – VoIP services market is predicted to expand 10 % every year until 2021 and touch $140 billion.
What is VoIP (Voice over Internet Protocol)?
VoIP services use Internet connections to make phone calls. The analog voice signal is turned into data packets and transmitted over the Internet, enterprise local networks or Wide area networks. Apart from voice data, VoIP also transmits multimedia content over IP networks.
How does VoIP work?
VoIP has become an increasingly popular choice for business communications and provides a stable alternative for traditional telephone networks known as Public Switched Telephone Networks(PSTN).
VoIP provides a reliable and secure communication channel with highly cost-effective models. To understand how VoIP can achieve this, one needs to look at the technology behind the services.
VoIP uses a codec to encapsulate audio into data packets and transmits them across an IP network and decapsulates them back into audio at the other end of the connection. VoIP uses standard codecs by the International Telecommunication Union, such as G.711 for transmitting uncompressed packets, or G.729 for compressed packets. This compression is typically used to decrease bandwidth requirements.
After it is encapsulated onto IP, voice data is transmitted via the real-time transport protocol or through its encrypted variant, secure real-time transport protocol. The most common communication protocol is Session Initiation Protocol (SIP) and is used for signaling that is necessary to create, maintain and end calls.
In an enterprise setup, VoIP emulates the traditional telephone networks with dedicated instruments – endpoints include applications running on mobile devices or dedicated desktop VoIP phones. VoIP is also available as a computer to computer service wherein you don’t need any extra hardware – calls can be made directly from the computer with just a microphone or a soundcard – the most popular example of this is Skype!
In many organizations, there may be an existing PBX system and VoIP system can use a SIP codec to connect with the PBX and allow it to manage user phone numbers; gateways to connect networks and provide failover in the event of a network outage.
VoIP networks have several other components such as session border controllers to provide security, call-policy management and inter-operator network connections. VoIP also has a host of additional functionalities which help users and management to operate smoothly – these are location-tracking databases for call routing and management platforms to collect call-performance statistics for voice-quality management.
Conclusion
A peek into the VoIP technology lays bare the reason for its popularity, especially among businesses – while cost savings may be one of the main reasons for migrating to VoIP (on an average, businesses can save between 50 – 75 % after switching to VoIP), businesses have consistently seen enormous jumps in productivity thanks to additional functionalities such as unified communication and telecommuting. In the current market scenario, where customers expect quick responses and a seamless customer experience is key to business success, VoIP has quickly become the only communication choice for most organizations.
As India’s first ICT Company to be listed on NASDAQ, Sify has years of experience in providing reliable and secure Network Integration services to enterprises across industry verticals.
Our cutting-edge networking services ensure reliable data connectivity services as well as the best-in-class Voice services in India – all available as cost-effective payment models aligned to scale with the growing needs of individual businesses.
5 Key VoIP features that Empower Businesses
During the early days of the VoIP (Voice over IP) technology, it was surrounded by skepticism over its long-term viability and its suitability across industries. However, the past decade has seen VoIP being firmly recognized and implemented across businesses of every size and industries of every nature.
VoIP in its current evolved form offers many such features that help provide increased functionality, cost-effectiveness, and improved efficiency. Beyond the basic options such as voicemail, call waiting and call forwarding, there are many strategic features that empower businesses.
Security
Security for its communications is fundamental for all businesses. VoIP offers that by adding a layer of security for all voice communications and encryption for media and other data. Most Voice over IP providers use Multiprotocol Label Switching (MPLS) at both ends, ensuring greater security for the users.
Mobility
VoIP solutions enable remote operation, giving the employees and managers, spread across vast geographies, access to constant and reliable communication, even when they are away from their offices. It reduces the requirement to travel, allows them to telecommute and increases team productivity. It also presents a wide reach across borders for the businesses at a nominal cost.
Scalability
As against a traditional alternative, where scaling up translated into expensive hardware and access to basic features entailed a minimum set-up size, VoIP uses the limited resources of money, space and manpower more efficiently. There is a reduced requirement for infrastructure freeing up physical space. There is a built-in flexibility of ‘pay per use’ that allows a business to scale up or down without the prohibitive expense of redundant infrastructure/ related software or the associated time to implement and operate the revised solutions.
Unified Communications
Unified communications (UC) fuses and brings together all corporate communication channels such as voice, chat, video, mobile and email as a part of a single integrated suite. UC, when linked with the right business processes, can dramatically amplify productivity. This is especially significant in industries with a sizeable and continuous customer interface as it provides customers with greater flexibility while communicating with the company. UC makes it possible for businesses to maintain a single easy-to-manage network instead of wrestling with different infrastructures for voice, data, and video.
Analytics
VoIP provides the businesses with an option for analysis of their interactions with their employees and the customers. The nature of the industry that these businesses operate in, determines the level of analytics that they need. However, the information is made available for all interactions with the VoIP solution. The analysis could be used to benchmark call efficiency KPIs, reduce turnaround time for troubleshooting, track call quality, agent or team specific metrics or even for compliance purposes. VoIP systems offer call recording and built-in reporting tools to support a business’ unique objectives.
These features and functionality offered by a VoIP (Voice over IP) solution can positively impact team productivity, customer relations, and core business operations. VoIP solutions can achieve this by enabling employees to work efficiently while juggling multiple devices, working from remote locations or constantly traveling for work.
Additionally, the constantly evolving nature of technology ensures that innovative new features are incorporated in the VoIP solution on a regular basis. As VoIP solutions ably support the new environment and scale quickly as the business grows or shrinks, it would have a significant influence on businesses over the next couple of decades.
As India’s first ICT Company to be listed on NASDAQ, Sify has years of experience in providing reliable and secure Network Integration services to enterprises across industry verticals.
Our cutting-edge networking services ensure reliable data connectivity services as well as the best-in-class Voice services in India – all available as cost-effective payment models aligned to scale with the growing needs of individual businesses.
Cloud Driving Transformation in the Healthcare Sector
The “Sify: Power Discussion” hosted at the “Healthcare Senate & Healthcare Information Technology Summit 2017” organised by the Indian Express Group and Sify Technologies discussed the various benefits that cloud can bring to the Indian healthcare sector.
The CXOs who participated in the power discussion hosted by Sify shared their challenges in the ICT space and subsequently, various views were shared by the panellists and Sify on how the cloud technology can solve their pain points and finally help in building better patient experience.
Summary of Challenges
- Increasing Data volumes is becoming unmanageable in preserving, optimising and retrieval of data. The Cost associated with that is also an issue.
- Can IT play a role in reducing the time of the patient in “Check-in / Checkout/ Post Checkout Care”?
- Challenges in the Inter-departments users of IT systems at the hospitals. For example, the HIS at times hasn’t been successful in reducing the pain points of the doctors with Care Teams.
- Disparate IT systems do not talk to each other and are not compatible, so there should be a common platform that allows different technologies to work seamlessly.
- Hospitals should prioritise in terms of what they want to achieve and accordingly how IT can play a role. At times, the perception is that IT has a magic wand, and any problem in hospital, IT is made a scapegoat.
The Case for Cloud Computing
Anindya Sen, Transformation – Evangelist, Sify Technologies, spoke extensively on how cloud can solve various challenges faced not only by the IT function but also the functions in the hospitals. He started with a specific example of the cloud implementation for the radiology department at Cancer Treatment Services International (CTSI). In each of the twelve CTSI hospitals, which were hitherto running on separate IT systems, were now completely moved on cloud. The data was now directly fed to the radiology departments of these twelve hospitals. It helped radiologists to serve the patients by doing targeted radiation.
One of the panellists asked about how cloud can reduce cost for the organisations. Cloud can significantly slash costs for companies who want to serve multiple locations using the cloud technology, however, the cost advantage might not fructify if it were a single location. Nevertheless, the benefits of cloud beyond cost parameters only were discussed for such scenarios.
A specific discussion happened in terms of healthcare industry where in spite of adopting Cloud, the IT team still has a task at hand in managing end points, their networking, etc. Network-as-a-service, a relevant example in this case was discussed to take the pain away from internal network management. Sify has provided “Network as a service” to many companies having a wide geographical presence using the cloud model.
The panellists were of the consensus that different components of IT like networks, applications, different patient systems etc. on cloud hosted by a single CSP, who partners with different domain experts and partners can unleash the potential that cloud can offer.
Sify explained a case study of Uttar Pradesh Power Corporation Ltd (UPPCL). Sify has hosted the IT infrastructure, end-to-end on cloud, partnering with the right domain experts and service providers for the various components of the IT infrastructure be it network, security, antivirus etc. The customer pays Sify on “Per Bill generated i.e. Outcome Based Model”.
With this model, the role of the CIO will focus not on “Switch on – Switch off issues” but concentrate on the Innovation, Patient Experience, Improve Inter-Departmental Coordination, Post Checkout Patient Care, etc. Various other models like per bed, per patient were also deliberated.
There is also a lot of potential waiting to be tapped in the on-premise cloud space. On premise cloud fits well with organizations having large IT resources in-house. IT and FMCG companies are a nice fit. Sify provides their infrastructure and services to these companies. This model was suggested by panel members specifically for concentrated IT landscapes.
With global issues like Global warming, floods are becoming more frequent and thus the availability of systems can get affected. One of the panellists spoke about how during the Chennai floods, because the systems were hosted in one place in Chennai, the hospitals in other cities were affected however in one of the similar instances of floods, this was avoided because now the systems were working on cloud. This brings in the case for DR as a service. Cloud can also be helpful in bringing innovation in IT processes.
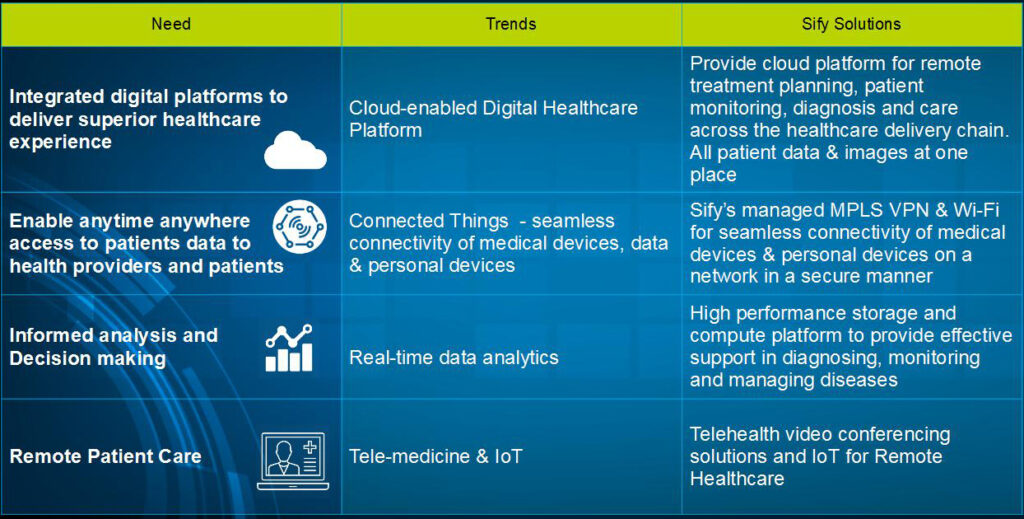
The Potential of Telemedicine
Telemedicine has not been able to take off in India and the reasons to which were discussed. Various suggestions on how telemedicine can be made more reasonable for the medical community and patients alike.
One of the reasons, as a panellist claimed, that was not allowing telemedicine to take off is there is no certainty on who will bear the cost. It works for the government, who pays for it entirely however for private hospitals, there is no business model.
Notwithstanding, telemedicine can be useful for patient scheduling, touchpoints, delivering care and administration process. There was also a broad consensus that telemedicine can be tremendously beneficial for secondary care i.e. once the patient has visited the doctor personally and his case is well understood by the doctor, the patient need not visit him the next time.
The treatment can happen using telemedicine unless it is necessary for an in-person visit. So the school of thought in the healthcare industry about the necessity to give the touch and feel for the patient is reducing and is a myth. With IoT technologies, the medical devices are also getting connected and this can be a contributing factor for the emergence of telemedicine in India.
Conclusion
On the whole, it was a good participative discussion where the various points of view from the Business side, IT side and the service provider angle were discussed. Obstacles as well as advantages for adopting an agile cloud based model were deliberated upon and a need for business outcome based model to help IT and business alike was unanimously agreed upon.
New technologies and solutions – such as mobile apps, cloud computing, the Internet of Things, and analytics – are available to make healthcare organizations more accessible, simpler, faster, and more cost effective.
Whether you represent a hospital, clinic, or specialist, Sify has a variety of scalable, agile, and secure solutions to help your organization achieve these goals.
Delegate Participants:
- Manoj Kumar (Apollo Health & Lifestyle )
- Santosh Patil (Asian Cancer Institute)
- Dilip Ramdasan (Dr. Agarwals Eye Hospital)
- Nallamuthu Sivaraj (Gem Hospital)
- Rajesh Kumar Gupta (Medanta – The Medicity)
- Jai Prakash Dwivedi (Rajiv Gandhi Cancer Institute & Research Centre)
- Ramesh Desai (Sagar Hospitals – Banashankari)
- Sachin P Marathe (Sapphire Hospitals)
- Niranjan Kumar Ramakrishnan (Sir Ganga Ram Hospital )
- Maneesh Agarwal (Apollo Hospitals)
- T S Mohan Kumar (Brindhavvan Areion Hospitals)
- Kvs Sesha Reddy (Brindhavvan Areion Hospitals )
- Ashim Kumar (CARE Hospital)
- Selwyn Colaco (Cytecare Cancer Hospitals )
- Naveen Nagar (HCG )
- Manisha Pal (Hiranandani Hospital)
- Paritosh Joshi (Kasturba Vaidyakiya Rahat Mandal)
- M. S Guru Prasad (Narayana Health )
- Manoj Chavan (Sir HN Reliance Foundation Hospital & Research Center )
Sify Participants:
- Subramaniam Ramakrishnan
- Anindya Sen
- Sonia Kaul
- Sanjay Gour
- Sagar Pattnaik
- Abhinav Gupta
Traditional vs VoIP- What’s best for your business?
As more and more businesses, both big and small, are jumping on the VoIP (Voice over IP) bandwagon, it is interesting to examine what is causing this exodus from the traditional alternative of PSTN (Public Switched Telephone Network) including Mobiles and Landlines.
In order to understand the reasons for the switch, it is important to first appreciate what is significant for these businesses while opting for a communication system. The chief concerns for businesses, irrespective of their size, while choosing a network are,
- How to reduce costs and at the same time not compromise on the quality of the communication system.
- Is there a way that would improve communication with customers and employees and better connect them?
- How to achieve more value for your money and get additional features at the same cost.
- Can the communication system contribute to an increase in efficiency and productivity?
As VoIP addresses these concerns and provides a powerful tool for businesses to ‘up their game’, enterprises in increasing numbers are opting for this alternative.
Cost-Effective Choice
A VoIP solution has a definite edge over its PSTN alternative as it offers free CUG (VoIP-to-VoIP) calling for both local and international. The calls made to mobile and landline phones through VoIP have nominal subscription fees as against a much more expensive PSTN alternative. The sound quality is continually improving as the technology is evolving, providing superior communications and better filtering of background noise with VoIP. Its online conferencing and other features help reduce the requirement for travel. It also has a lesser bandwidth requirement (10 Kbps) than the PSTNs (64 Kbps).
Improve Communication with Customers and Employees
VoIP provides unified communication, helping the employees to work remotely from any place with an Internet connection and ‘take the office’ with them. It also provides the ‘presence’ technology that enables users to see if employees are available and accordingly get in touch with them. PSTNs on the other hand, are able to provide the remote extension facility only with dedicated lines for each extension and hence are very expensive.
More Value for Money
VoIP solution provides an ease of scalability without adding significant infrastructure and cost to the decision. Additionally, VoIP offers call waiting, call forwarding and call transfer options as a standard offering, but the same is available in PSTNs at an additional cost.
Increased Efficiency and Productivity
VoIP has an edge over its traditional counterpart as it allows businesses to get enterprise class software at an affordable cost. As the cost of scalability is low, even smaller businesses can enjoy customized solutions with many features as standard or as an affordable add-on. These lead to increased productivity, less down time, and hence more profit. However, as the service terminates when the Internet connectivity (power) is lost, organizations must have a VoIP backup plan. PSTNs, nevertheless, are able to continue service during power outages, as phone jacks do not require electricity.
Hence, traditional choices such as PSTNs are making way for VoIP as the latter are proving themselves as a powerful tool, giving the businesses a competitive edge and providing the ‘right-size’ technology at an affordable price.
As India’s first ICT Company to be listed on NASDAQ, Sify has years of experience in providing reliable and secure Network Integration services to enterprises across industry verticals.
Our cutting-edge networking services ensure reliable data connectivity services as well as the best-in-class Voice services in India – all available as the cost effective payment models aligned to scale with the growing needs of individual businesses.
CCaaS – Using technology to enhance customer engagement
The business world has always been competitive, but never before has the battle for customer loyalty been fiercer.
Organizations are plowing in more money and effort to step up their customer care strategies and with good reason! Reports and surveys reveal the importance of customer engagement in buying decisions – 86% of the consumers are willing to pay more for better customer service and 54% of Millennials say that they stopped doing business because of poor customer service.
In these competitive times, businesses have turned to technology to get the most out of their contact centers and to provide a pleasant customer experience to buyers.
When it comes to using technology to optimize Contact Center functions – CCaaS (Contact Center as a Service) instantly springs to mind. It is the perfect example of using cloud-computing platforms to integrate the latest technology with your contact center while keeping costs low.
Contact Center as a Service – Key Technologies
Inbound & Outbound Call Automation
There is a great deal of technology behind every call that comes into a call center. Some of these are automatic call distributors (ACD) – intelligent routing of calls to agents, IVR (Interactive voice response) – automated phone system providing information to callers, voice biometrics, intelligent call back, universal queuing, call recording and now, of course, integration of multiple communication channels to provide customer engagements across all platforms.
For agents making outbound calls, technologies such as predictive dialer – automatically dial from a contact list, campaign management systems and email response management software helps in increasing productivity.
System Integrations
With services like CCaaS, contact centers can access a wider level of integration across the organization. From integrating existing knowledge database (comprising customer profiles, call histories, buying trends, etc.) to business CRM software – access to a plethora of information allows agents to serve customers better and faster. CCaaS also facilitates secure online payments via integration with bank websites and bank mobile applications.
Quality check and Admin Control
Call monitoring and call quality control has now been enhanced by adding new systems such as an administrative control dashboard with a range of web supervisory features from silent monitoring to whisper coaching. Supervisors can now observe and step into help agents and prevent unpleasant experiences.
Analytics
With the explosion in Internet usage, data analytics tools are becoming more and more refined and for predicting customer behavior, contact centers must also utilize analytical tools to better understand customer feedback and needs. While all contact centers use real-time reports & analytics to evaluate and improve agent performances, there is also a move towards incorporating speech, chat, and text analytics to identify customer needs.
Customer experience is all set to overtake product and price as the most vital component of the business strategy by 2020.
There is no doubt that with the rise of social media and increasing use of Internet, more choices have opened up for buyers and they have become more aware and better informed. Organizations are well aware of this and are investing more and more in gaining and retaining customers – along with enhancing the human interactions by providing the right training, integrating technology is the only way organizations can hope to handle the huge volume of multi-channel customer contacts, smartly while being cost-efficient.
The trends and technologies shaping the future of Contact Centers
Contact Centers are in a state of constant evolution! With customer engagement rated as one of the most critical factors for the success of a product or service, businesses are striving to perfect the customer care scenario every single day. In this race to keep customer loyalty, companies are turning to technology to deliver exceptional customer service.
In the last couple of years, to keep up with the changing needs and behavior patterns of buyers, Contact Center technology has evolved considerably. We take a closer look at some of the latest trends in the field.
The trends and technologies shaping the future of Contact Centers
Digital Transformation of Customer Services
The digital way of working has now been fully embedded into the business operations of most companies. As newer technologies such as cloud, web based applications, mobility, and data analytics change the business landscape they also have an impact on how contact centers are operated. Adoption of these technologies, especially the move to cloud platforms, has resulted in altering the entire cycle of customer engagement – from dealing with the first client contact occurring across multiple channels to providing intelligent, data analysis backed the resolution to customer issues.
Omni channel Models
From traditional phone calls to social media messages – Customers are using a variety of communication channels to approach businesses. Needless to say, businesses are also turning to a more holistic customer engagement approach that uses unified Omni-channel communication models – bringing text, phone, chat, email, social, video calls, etc. under one umbrella – to provide a more personal and satisfying experience to the customer.
Analytics and Customer Satisfaction
To consistently deliver exceptional customer experiences, businesses need to consider more than the final resolution of the customer requirement; it is imperative to keep a check on the customer experience during the journey towards resolution and overall quality of the calls. This can be achieved by using analytical tools to improve the Contact Center operations. Customer care centers are using real time reports and monitoring solutions to keep a check on engagement quality and are also incorporating cutting edge analytical tools to study behavioral patterns in speech, text or chats to predict customer behavior.
Remote agents
With reliable web based communication tools and access to real time monitoring Contact Centers are now employing more and more remote agents; thereby efficiently managing different time zone requirements while reducing overhead costs.
Artificial Intelligence
AI, the latest buzzword in the IT landscape, is now being tested and incorporated in Call centers as well. AI algorithms are mainly being used to analyze call data and historical records to foretell customer behavior – producing dependable results in minutes, something that would have taken an analyst days to complete. AI technology is also being explored to place virtual call agents to handle some of the more repetitive and simpler customer interactions.
Going ahead, companies and consumers alike will be putting more and more emphasis on customer care as a brand differentiator rather than as a support function. Although recruiting and training agents form a vital part of call center operations; to stand out companies are exploring technology integrations to make their operations more efficient. And while technologies like Artificial Intelligence are still being developed and implemented, sophisticated cloud based offerings such as CCaaS (Contact Center as a Service) are proven models, which bring an added level of productivity with enormous cost benefits to traditional Contact Centers.
As India’s leading fully converged ICT Company, Sify is using its decades of experience in network and Data Center services to present the most comprehensive Contact Center as a Service platform in India.
Our extensive expertise has allowed us to craft a service offering, which is highly flexible, scalable and future proof. Sify’s CCaaS provides all Contact Center applications under one umbrella-from branch connectivity and video conferencing to 100 % reliable voice calls. Delivered via the cloud, Sify’s CCaaS is a multi channel platform, which can easily meet the most exacting contact center requirements.
3 Key Benefits of taking your contact center to the cloud (CCaaS)
The key to thrive in a “Customer is the King” economy is being extremely responsive to their ever-evolving demands while serving as a pacesetter for the competition. Customers are demanding a wider choice of contact channels, stronger relationships, flexible customer service options and quick-to-respond customer service. All these factors have increased the pressure on Contact Centers; they must deliver the best possible customer experience – consistently!
Organizations are progressively moving towards ‘as a service’ technologies as they look for models that are flexible and enable better responsiveness and service quality in today’s customer centric environment. Contact center service providers’ cloud-based offerings focus on cloud as a deployment option as against the conventional on-premise alternative. By taking the contact center to the cloud, businesses get a robust, flexible, cost-effective and multi-channel solution with unified delivery and professional management.
3 main Benefits of Cloud-based Contact Centers
Flexibility and Scalability
A traditional contact center is based on the intended contact service agent capacity, the approximated volume of customer interactions and an estimate of the type of channel/feature access required. On the other hand, cloud solutions enable businesses to operate fluid contact center operations, where they could modify the scale of operations, swiftly add functionalities, switch the mix of communication channels, handle unanticipated spikes in the interaction volume or draw on enterprise resources. Flexibility and scalability afford unlimited possibilities almost instantly to the businesses without the prohibitive expense of additional infrastructure/related software and the associated time to implement and operate the revised operations.
Substantial Cost Savings
Cost arguments in favor of cloud solutions versus traditional Data Centers are apparent right from the start – the former helps transfer the financial load from CAPEX (Capital Expense) to OPEX (Operating Expense). Switching to an OPEX model brings with it more simplicity and predictability with a ‘pay-as-you-go’ model. It eliminates the challenge and risk of making large capital expenses towards infrastructure at one given point; making it easier to budget for growth. In comparison, non-cloud contact centers cannot achieve this desired flexibility without investing a sizeable amount in infrastructure and are unable to facilitate businesses to right-size their operations. Cloud solutions are cash flow friendly as recurring costs are coupled only with an associated growth spike, thus eliminating the risk of unutilised investment. It also allows better budgeting, planning and related staffing decisions resulting in increased efficiency and productivity
Streamlined IT
Software-as-a-Service (SaaS) has been an industry norm for core applications like email/ CRM and many other business applications and is increasingly becoming universal. Cloud solutions guarantee that bandwidth, network and other communication services are addressed in order to meet evolving business needs and adapt to rapid changes in the business. The cloud-based contact center solution is hosted in a secure and reliable environment, as a result saving time and allowing businesses to focus their energies on their operations. There is an additional benefit of 100% reliable backup and disaster recovery of data and applications, which is difficult and expensive to implement and execute at a smaller scale. Taking their contact center to the cloud provides the businesses with an assured level of business continuity and the option of long-term retention of the data in their contact center operations. Leaders are becoming progressively more interested in the cloud adoption in this model and the operational agility benefits that it provides.
One constant for the contact centers is their relentless pursuit of change for the better. They are continually looking for superior technology, more efficient processes, and better-trained resources in order to improve the quality of the customer experience. These are aimed at serving customers more effectively and at the same time more economically. As providing exceptional one-on-one service, regardless of the medium, becomes the norm for businesses; cloud solutions for the contact centers serve the need of the hour by making it affordable to provide customer experiences designed to make buyers loyal to the brand.
As India’s leading fully converged ICT Company, Sify is using its decades of experience in network and Data Center services to present the most comprehensive Contact Center as a Service platform in India.
Our extensive expertise has allowed us to craft a service offering, which is highly flexible, scalable and future proof. Sify’s CCaaS provides all Contact Center applications under one umbrella – from branch connectivity and video conferencing to 100 % reliable voice calls. Delivered via the cloud, Sify’s CCaaS is a multi channel platform, which can easily meet the most exacting contact center requirements.
How CCaaS can help businesses create a compelling customer experience
Contact centers are evolving as the pivotal point of customer interaction across multiple touch points. For businesses, creating a compelling customer experience is about building robust relationships by seamlessly engaging with them through varied channels. Contact Center as a Service (CCaaS) helps create such elevated experiences consistently. Additionally, these solutions also increase productivity, improve efficiency and reduce costs.
With the ability to transform businesses’ interactions with their customers and CCaaS’ myriad benefits, it is of utmost importance to choose a solution that is both financial as well as operational ‘right fit’ for the organization. Therefore, to define what constitutes an able CCaaS solution is of great significance.
Key Features of CCaaS Solutions
Through CCaaS, a business can look forward to the following:
- A complete set of multi-channel, dynamic Interactive Voice Response (IVR) and routing capabilities. CCaaS solutions offer an efficient inbound and outbound call center routing. It includes centralized Automatic Call Distribution (ACD) with Skill (Multi) based routing that manages incoming calls and processes them based on the number called and the database of handling instructions. This Intelligent Routing adds to the customer experience as it leads the customer to the most apt agent. It also offers other Automated Features such as the Call Back Manager. Furthermore, in a multi-cultural context, such as India, a CCaaS also offers speech integrations for several regional languages
- Customers want to connect via their preferred channel be it in person, through e-mail, social media or voice, at the same time organizations, want efficient usage of their agent resources. This is made possible through configurable and customizable unified web-accessible agent desktop, which helps reduce the Average Handle Time (AHT) as it helps the agent handle all types of interaction with a single interface, increasing their efficiency
- With its multi-site offering, it presents inherent location independence and lets a business manage and report on agents/ supervisors from anywhere. Additionally, it offers a multi-location multi-channel architecture that provides organizations with branch connectivity solutions
- In the current business context, analytics play a vital role. Centralized Reporting enables reporting analytics of the contact center interactions, which supply data that help organizations take more informed business decisions.
- The flexible platform simplifies integration with CRM and other business applications or platforms for better customer experiences. It promotes increased productivity as it reduces execution time and allows faster roll out of campaigns. In addition, the solution can be tailor made to the organization’s configuration and settings with a powerful administration interface.
- Quality Assurance is ensured through call monitoring/recording through its Voice Logger/Recorder Solutions and Quality Monitoring Solutions, resulting in consistent customer interactions.
- The solution is Cost-Efficient, owing to its ‘pay-as-you-grow’ OPEX (Operational Expense) solution as against the traditional CAPEX (Capital Expense) model. It affords the business flexibility, scalability and the ability to access services such as disaster recovery and data backup, which might otherwise be cost prohibitive.
- By opting for a Managed Solution, businesses can focus their energies on their core operations while the CCaaS platform is managed and maintained by the experts. Organizations are assured Quality of Service (QoS), reliable network and updated technologies without any extra effort or cost.
Customer interactions are complex and fluid. CCaaS is an attempt at equipping businesses with tools that can help them engage, manage and reflect on these exchanges to enhance customer experience to create long-term and loyal brand followers.
As India’s leading fully converged ICT Company, Sify is using its decades of experience in network and Data Center services to present the most comprehensive Contact Center as a Service platform in India.
Our extensive expertise has allowed us to craft a service offering, which is highly flexible, scalable and future proof. Sify’s CCaaS provides all Contact Center applications under one umbrella – from branch connectivity and video conferencing to 100 % reliable voice calls. Delivered via the cloud, Sify’s CCaaS is a multi-channel platform, which can easily meet the most exacting contact center requirements.
Contact Center as a Service – What is it and how can it benefit your business?
Customer is king and in today’s cutthroat and unpredictable marketplace keeping your customers happy and loyal is vital for running a successful business.
The first call, the first mail, the first comment on social media – whenever customers want to communicate, a business Contact Center is the first port of call. They are at the forefront of customer engagement and it goes without saying that, this part of any organization must be staffed and operated with utmost care.
Organizations are, of course, fully aware of the importance of running a good contact center and are now turning to new technologies to reduce negative customer care situations. One of the most popular and cost effective methods to streamline and automate the process is by opting for CCaaS – Contact Center as a Service.
What is Contact Center as a Service?
A completely novel way of using the best and the latest technology to provide world class customer engagement from your contact center. CCaaS provides
Cloud-based contact center solutions that allow businesses to deliver outstanding customer experiences via any medium.
These days it is fairly common for customers to approach organizations from a multitude of channels – while voice calls remain the most popular method of communications; companies need to keep all the other channels – email, social media, text etc – open and manned to provide a truly comprehensive and differentiated customer service.
With CCaaS, businesses can purchase and integrate the latest contact center technology with their existing systems (or set up a new contact center from scratch). CCaaS leverages the power of the cloud to offer a complete solution that includes services such as automatic call distribution, dialer, logger, multimedia or omni channel capability, all of which can be ramped up or down on demand.
How can businesses benefit from CCaaS
Whether your business is setting up a new contact center or refreshing the existing contact center technology, the advantages of opting for a CCaaS package are too numerous to ignore.
Costs – the cost benefits of using CCaaS is obvious right from the start. Business no longer needs to invest in infrastructure – delivered via the cloud, Contact Center as a service does away with the need to invest in routers, servers, and similar infrastructure. The easy pay-per-use model makes it even more attractive as it allows companies to pick and choose the pricing that works for their budget and requirements.
Flexibility – as-a-service model allows for dynamic scalability. With CCaaS companies can add agents or deal with sudden workload spikes instantly. CCaaS allows almost instantaneous ramping up or down of resources to match the client’s needs.
Analytics – organizations can access real-time monitoring and detailed reports of every part of the contact center. These insights are critical for understanding the gaps in service and productivity of agents, providing a foundation for enacting key changes.
Better Customer Experience – the CCaaS technology enables organizations to serve their customers better – multi-channel coverage allows for a more engaged customer outreach, intelligent caller profiling allows for quick resolution of the problem and real-time supervision of agents and calls can improve the quality of the interaction.
We are living in the times of soaring choices and hyper-informed consumers. To retain customers and ensure brand loyalty business must provide an out of the world customer experience.
Customers, nowadays, expect to be able to interact with organizations, when they want, how they want and with consistency in their service response and the only way to manage this complex communication scenario is by bringing in the latest technology.
Transform the corporate workplace with Managed WLAN
When it comes to Internet connectivity in an organization, user expectations are sky high! Employees and guests, alike, expect fast, secure and highly available WLAN services the moment they step into office premises. To match this growing demand, several organizations have opted for subscription based Managed WLAN services.
Apart from easing business operations and enriching the corporate work culture, Managed WLAN services contribute directly to business productivity and profitability. To better illustrate the scope and benefits of an outsourced cloud based Wi-Fi setup we look at how an ITES enterprise can be transformed by managed WLAN services.
Challenges and Needs
In a large global company with thousands of employees spread across various regional offices in India, WLAN systems are complex projects that require dedicated management and support.
For an enterprise spanning vast geographies, the challenge is to provide secure and reliable Wi-Fi Internet access to users in all the regional office across the country. The enterprise would also require dependable connectivity at a desired bandwidth to ensure a certain speed for executing business critical functions.
What does a managed WLAN service provider bring to the table?
Managed WLAN services is so much more than providing access and managing corporate users, it’s a 360° process that starts right from the design phase – a team of Network experts study the organizational layout and its bandwidth requirements and design a WLAN plan based on their analysis.
The technology partner will then start the engineering and installation process. This includes –
- Installing an Internet link of required bandwidth, based on the number of users expected to access the Internet.
- Deployment of Wireless Access Points at all corporate branches, including cabling and PoE injectors/ switches.
- Configuration of wireless SSIDs.
- Building a customized corporate homepage with access control through user login.
Once the WLAN system is in place, the solution provider takes over the daily management and monitoring of the Wi-Fi ecosystem. This takes the form of –
- A cloud based centralized WLAN monitoring console to observe the network and detect, prevent and mitigate wireless attacks. The client is also able to gain 360° network visibility and user–level and application-level control.
- A centralized authentication system to provide network access based on users, devices type and location.
- A guest management portal to provide access to guests and temporary users.
How does Managed WLAN transform the corporate workplace?
After implementing a managed WLAN solution, the first and the most perceptible benefit is seamless and smooth connectivity for all users. Employees and guests alike can now bank on reliable wireless connectivity that can be accessed easily.
A managed WLAN service also frees up the core IT personnel from the daily operations of network management, giving them time to focus on areas of strategic business importance.
The network managers are also given complete network visibility and control. Along with being able to easily control the bandwidth and access, the managers are provided metrics and reports on Internet usage among employees or guests and performance and usage of applications.
In conclusion
From large global organization to SMEs, the rise of mobile usage and BYOD culture has changed the significance of Internet connectivity in a corporate setup. To provide secure, scalable and seamless Internet access, professional solution providers must be brought into the picture. The increase in productivity and efficiency that a fully managed WLAN system brings to an organization equals a positive Return on Investment.
For more than a decade, Sify has been successfully building and managing complex networks ecosystems across the globe. From commissioning the world’s largest MPLS network to leveraging cloud platforms for enhancing connectivity – Sify has the deep domain knowledge across the entire length and breadth of the network landscape. This experience gives us an in-depth understanding of what enterprises require from their networks and how they use them.



































































