Embarking on a successful Microsoft Cloud journey with Sify
In the digital age, migration to Cloud has become the top-most priority for businesses across realms. We are seeing major shift in the number of ‘Cloud Hostile’ customers turning into ‘Cloud Friendly’ & ‘Cloud Ready’ customers and pondering on the best plan to implement the migration successfully.
Know more about Sify’s offerings in the cloud migration services space.
One of the major reasons behind this trend – besides performance, security, and cost – is agility & flexibility which help in faster business innovations. Organizations have started transforming themselves digitally to drive business value and grow business with enhanced end user experience.
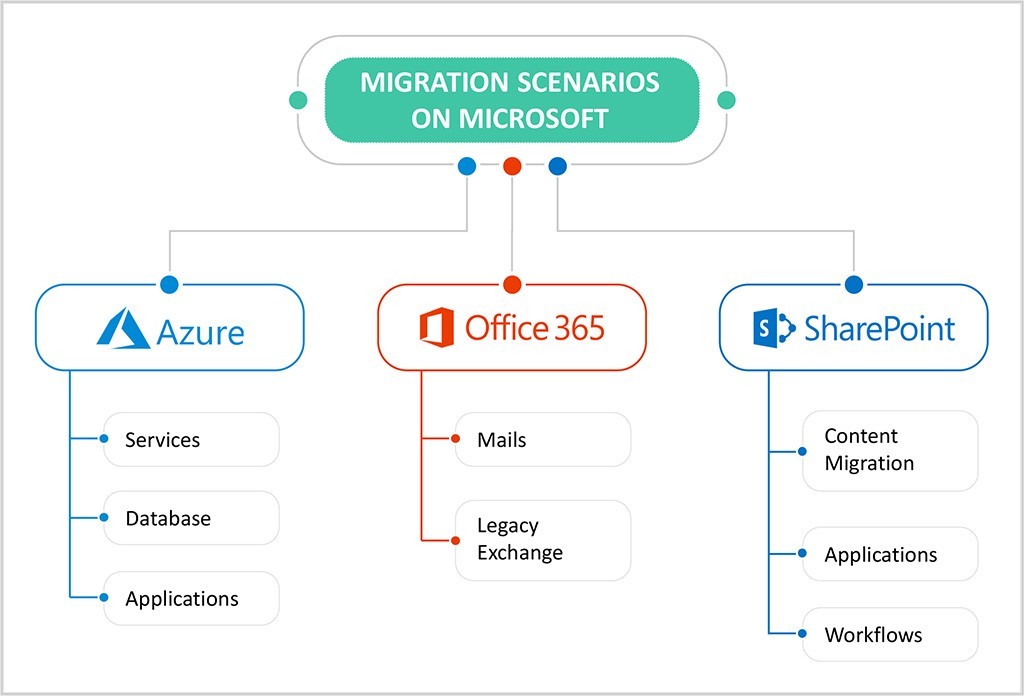
Over the past few years, Microsoft has earned massive popularity among organizations worldwide for being a leading Cloud and cloud managed services provider with – Azure, Microsoft 365 (M365) and Microsoft Dynamics 365.
Microsoft Azure is a highly productive, hybrid, and intelligent Cloud that allows you to leverage the power of cutting-edge digital technologies to build, deploy and manage critical applications as per your company’s requirements. It also provides Cloud enhanced services like AI/ML, RPA, Analytics tools, and integrated Cloud resources to make your organization more agile and improve top-line performance.
Learn more about Sify’s capabilities in the Microsoft Azure managed cloud services domain.
Considering the above benefits, many forward-looking businesses are exploring Azure Cloud-powered services and Azure managed cloud services to optimize internal processes and generate new business models. However, this digital aspiration is incomplete without transforming the technology landscape first. A strong technology foundation provided by Microsoft will help you connect your disparate data, processes, users, and applications to accomplish the end objective of organizational excellence.
Achieving all these is not as simple as it may seem initially! That’s where, Sify’s consultative approach and Azure managed cloud services capabilities can help you leverage the true value of Microsoft Services and align your organizational roadmap with the ever-evolving technology landscape.
Explore why Sify ranks high among the leading cloud managed services providers across the globe. Know more about our public, private, multi- and hybrid cloud managed services capabilities.
Azure Migration: The most successful path
Different organizations have distinct approach towards Cloud migration and need different types of cloud migration services, and their decisions are governed by business specific priorities and constraints. You must know that Cloud migration services involve significant organizational change management across people, process, and technology. It’s very important to draft a holistic approach to migrate successfully and realize the benefits of efficiency, agility, and cost.
Sify’s cloud migration services for Azure
As a trusted partner among cloud managed services providers globally, Sify offers unmatched capabilities in cloud migration services. With Sify as your strategic partner for cloud migration services, you are perfectly positioned to draft, implement, and monitor the overall migration plan in the most successful way. Our team of Cloud experts, Azure certified professionals, cutting-edge toolchains, and partner ecosystem can help you accomplish migration goals successfully. Our cloud migration services can help you across all three phases of migration – assessment, migration, and optimization.
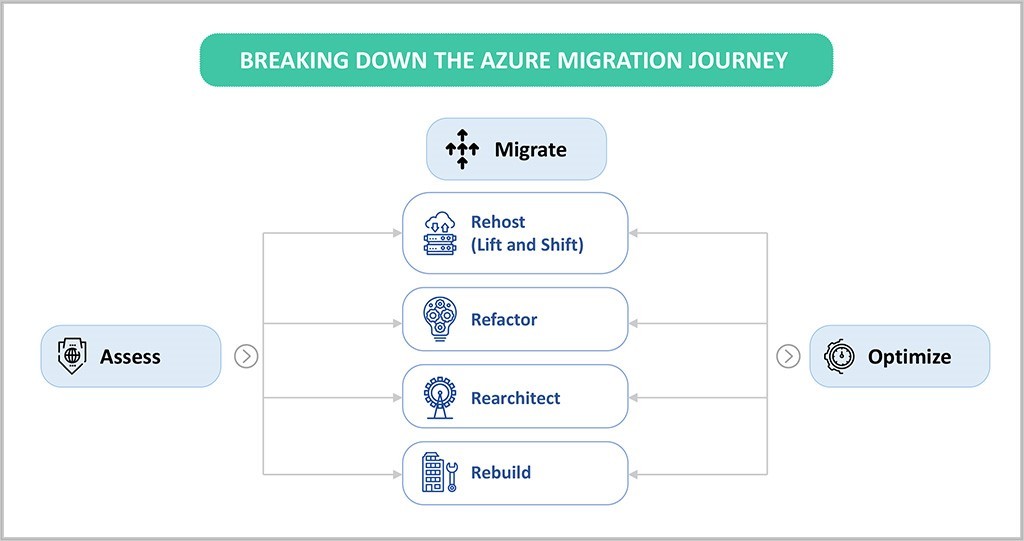
Assessment: This is the first phase of migration journey, which includes assessing and discovering your on-premises apps, data, and infrastructure. Our comprehensive range of cloud migration services and assessment services can help you map dependencies across applications and decide their priority of Azure migration for a seamless journey.
Migration: The actual cloud migration begins in this phase, where you start moving your apps, data and infrastructure – leveraging the best-suited cloud migration services, strategies and tools. Our cloud migration services will help you automate the entire migration journey (depending upon your IT specific needs) and minimize the downtime.
Optimization: Once you have moved to Cloud, it becomes important to monitor your Cloud resources continuously for better performance, enhanced security, and reduced cost. Consistently ranked among the leading cloud managed services providers, our managed services will help you maximize your ROI and leverage unified visibility of Cloud resources for efficient resource utilization and optimization.
Explore how Sify’s cloud migration services bring the assurance of high rates of success. Know more about our public, private and hybrid cloud managed services and migration capabilities.
Sify + Azure Advantage
- Single window solution provider (Network, Security, Azure IT and Management)
- End-to-end Azure service coverage: Access – Architect – Migrate – Manage – Secure
- Integrated Azure network and security proposition
- Unified Dashboard across Azure IT
- Simplified Execution and single point of ownership
Know more about transforming your IT Infrastructure with Sify’s Microsoft Azure managed cloud services capabilities.
Microsoft 365 – Mail migration
With Office 365 becoming the de-facto mode for conducting business, it is important to modernize the underlying infrastructure and platform. It is imperative for enterprises to move their legacy exchange and other mailboxes to Office 365 in order to reap full benefits of their workflow optimizations. Additionally, Office 365 offers the benefit of pay per use pricing for optimizing cost.
So in case, you are exploring the possibilities to conceptualize and implement your cloud migration in the most success-driven manner, Sify can help you embark on a successful Microsoft Cloud journey.
Our Accreditations
- Microsoft Certified Partner for Cloud & Managed Services
- Certified Deployment Partner for deployment of M365 & Azure services
- Express Route Partnership for seamless connectivity with MS Cloud Azure & Microsoft 365
- Certified team for Migration & Deployment of MS SQL workloads
- Certified team for deployment of Hybrid Cloud Platform
Simplify Your Network Transformation
Simplify your Network Transformation with Sify
The business world is witnessing an unprecedented transformation as organizations across verticals are passionate to embrace new technologies. Cloud, Analytics, Automation, Internet of Things, Artificial Intelligence, and Machine Learning are some major forces that are enabling enterprises to deliver a top-tier experience to customers. As organizations nowadays are highly reliant on these emerging technologies to achieve organizational excellence, one must acknowledge that all cutting-edge technologies require an intelligent and robust network. There are numerous factors that are fundamentally redefining the ways new-age networks work and function. The emergence of new global trends and multiple new technology trends have compelled organizations to demand more from networks. This blog discusses:
- Major global and technology trends that have paved the way for network transformation.
- New-age network architecture and design for Intelligent Network services
- How Sify can help you in your network transformation journey with a wide range of Intelligent Network Services.
Global Business Trends leading to increased demands from Networks
- Hyperconnected Enterprises:
In the digital age, global organizations rely on a multitude of connections for geographically distributed people, processes, and devices. Also, the increasing adoption of hybrid and multi-cloud has compelled global enterprises to become hyperconnected. For such hyperconnected enterprises, a scalable network is quite critical to deliver top-tier services to customers across the globe through digital technologies. - Digital Business Transformation:
In line with their digital ambition, organizations worldwide are looking to leverage Cloud-native technologies such as analytics, mobility, IoT, AI, and ML to modernize and develop new processes, services, and models for generating new revenue streams. An intelligent and adaptable network can quickly adjust according to evolving requirements, facilitating seamless transformation. - Automation and Robotics:
Several enterprises rely on Automation, Robotics, and Robotic Process Automation to improve operational efficiency, quality of services, and customer satisfaction score. The use of Automation and Robotics in the coming years will continue to surge as companies look to improve quality, workforce productivity, customer satisfaction, and more. This is even more relevant than ever in the pandemic-stricken world. As automation of processes is time-sensitive and mission-critical, enterprises will need round-the-clock availability and reliability from their distributed networks as even a minor lapse in network availability or reliability can potentially hamper the process flow and affect overall efficiencies and customer satisfaction.
Technology Trends powering fundamental Network Transformation
- Applications being modularized and distributed across Clouds: Recently, hybrid Cloud and microservices have gained massive prominence across business verticals. The majority of software applications are being modularized and distributed across public Clouds and network edge. To support applications across such a distributed landscape, the network needs to transform fundamentally. There is a need for Networks to be agile, seamless, secure, and responsive to dynamic application landscapes.
- IoT and M2M integration with mainstream Networks: The exponential rise in the number of IoT devices worldwide highlights the need for smart Machine-to-Machine communication. This means the network must capably provide connectivity to all the IoT devices and integrate them smartly with mainstream networks.
- Pervasive Mobility: Owing to the anywhere data center and anywhere user access, there is a need for a robust network to allow users to access applications on Cloud. As anticipated, mobile users will continue to grow in the years to come and they would need round-the-clock high-performance connectivity to access applications on Cloud from private devices over Wi-Fi or 4G networks. Therefore, to cater to this rapidly growing mobile population, it becomes imperative to strengthen the Edge connectivity to these vast diverse, and distributed user base. Edge Transformation is predicted to be the next big wave in the Networking space. As per Gartner – by 2025, 75% of enterprise-generated data in industrial settings will be created and processed at the edge.
- Immersive video experience: User experience has taken the center stage in the digital era, therefore enterprises are keen to make the video experience more immersive. They have started leveraging the power of digital media technologies, Virtual Reality, Augmented Reality, and immersive 3D environments to ensure a top-tier experience. This is placing greater demands on enterprise networks as video experience is totally dependent on low-latency and high availability infrastructure. Moreover, enterprises also want their networks to provide end-to-end bandwidth and dynamic performance controls to further make the experience more enriching.
New-age network architecture and design for Intelligent Network Services
In response to emerging trends and the fast-changing IT landscape, organizations need to rethink network architecture and design strategies to drive digital transformation. It becomes quite critical to align network capabilities in accordance with the changing business requirements and modern topologies. In this light, some of the expectations from Intelligent Network Services are the following:
- Support the fast-changing set of users, applications, devices, and services and unify them intelligently for top-tier user and application experience
- Seamlessly connect between distributed IT assets and applications in a DC and hybrid multi-cloud environment
- Leverage Software and other functionalities to control, rather than physical access and distributed policy control
- Leverage the cutting-edge technologies and algorithms to collect, assimilate, analyze, and visualize networking information in real time for better visibility and control
To achieve the above objectives, there are 3 broad aspects that the IT leaders must follow while designing and architecting the new-age network architecture.
Networking architecture for anywhere Data Center:
Organizations nowadays have their applications and data spread across Data Centers, Clouds, and Edge environments in diverse geographical regions. To meet the requirements of this diverse hybrid ICT landscape, organizations need new networking architecture that is ready for Cloud, meets application connectivity demands, and ensures technology and operational consistency across locations. Therefore, the new-age network must facilitate faster and safer modes of data transfer across Data Centers, Cloud, and Edge devices. This highlights the significance of Cloud-ready Networks with DC Interconnects and Cloud Connect capabilities.
Being a trusted ICT company, Sify ensures a Cloud-ready Network, comprising of Data Center Interconnects, Hyperscale Cloud Connects, and Internet Exchanges for carrier neutrality. Our Cloud-ready Network provides you with deterministic and secure connectivity to move applications, middleware, and database workloads between private infrastructure and Cloud for improved application performance.
Hybrid WAN and Application performance-focused Network Architecture:
In the age of hybrid and multi-cloud, it becomes critical for organizations to have a well-thought-out network strategy for distributed workloads, data footprints, applications, services, and microservices. With the rise in multi-cloud adoption, the legacy hub-and-spoke WAN architecture can hold organizations back. The shift from Data Centers towards Cloud has resulted in the more prevalent use of the SLA-defined Internet (in addition to MPLS) as a reliable and pervasive way to establish robust connectivity. Hence, modern-day businesses need a hybrid WAN strategy – the use of internet for business applications along with MPLS. This means the new-age network must enable the hybrid WAN and be smart enough to adapt to the changing application performance demands in a hybrid or multi-cloud environment, ensuring better performance.
Herein, Software Defined Networking can enable fundamental network transformation. SDN can help accomplish the goals of network transformation – agility, flexibility, and application centricity – by intelligently controlling the network architecture using software applications.
- Software Defined Networking facilitates flexible network architectures, which can utilize multiple network connectivity options (MPLS/ILL/BB/4G-LTE/Internet) which help leverage a Hybrid WAN strategy for the evolving DC and Cloud landscape
- SD-WAN ensures application awareness and complete visibility of site-wise utilization of various applications, which paves way for better performance, availability, and security.
- SD-WAN leverages the power of Cloud-based monitoring and management platform for centralized, real-time visibility of all resources.
- SD-WAN solutions can be easily integrated with legacy network architectures, which enable phase-wise migration of sites.
Sify’s SD-WAN platform is hosted in Secure Cloud, and our experts perform all the monitoring and management functions from the state-of-the-art NOC. This helps you maintain distance with different configuration tasks at branch sites and focus on your core business. Our SD-WAN solutions – coupled with end-to-end Managed Network Services – drive efficiencies, reduce cost, and optimize multi-cloud connectivity.
Centralized visibility, control, and insights of the Network:
Organizations need complete visibility and control over network connectivity to make the most of their Cloud investment. They would also want their network to provide intelligent insights that enable data-driven decision-making. An intelligent network can help businesses with automated and effortless orchestration of network resources. However, enabling a network with comprehensive intelligence is not as simple as it seems, because it requires a well-established network management practice with well-integrated toolsets.
Currently, only a few network service providers, such as Sify Technologies, have the assets, capabilities, and expertise to deliver Intelligent Network Services. We ensure centralized management of the network, powered with the capacity of SDN, to bring in the highest level of visibility and control of the entire network landscape. We offer a comprehensive range of Network Management Services on flexible outcome-based models – shared NOC Services, Hybrid NOC Services, and Dedicated NOC Services – from our state-of-the-art Network Operating Center.
Sify’s network experts ensure 24×7 proactive monitoring and management of network connectivity of devices such as routers, switches, and firewalls, and provide comprehensive reporting of various network parameters such as availability, performance, and security.
Conclusion
The emerging business and technology trends have compelled enterprises to empower their network with inherent intelligence built into them. This needs fundamental network transformation and re-architecting from the ground up, to suit evolving DC and Cloud landscape, distributed/mission-critical applications, and network orchestration needs.
Being a strategic network transformation partner, Sify helps you transform your network into a robust and intelligent asset. We provide Intelligent Network Services which include Cloud-ready Networks, Software-defined WAN, and centralized Network Managed Services, to accelerate your digital transformation with the robust foundation of a fast, secure, and future-ready network.
Simplified Cloud Adoption for SAP S/4HANA
Let Sify, your Cloud expert manage your SAP Migration
Every transformation journey begins with adoption of digital technologies on Cloud. Forward-looking organizations worldwide are looking for Cloud-powered solutions to attain the highest level of business agility, scalability, and compliance in the most cost-effective way. Additionally, Cloud-powered solutions facilitate access to new generation technologies, such as IoT, AI, and ML, which help you achieve your transformation goals in an outcome-focused manner.

SAP S/4HANA is a modern business solution suite that fosters intelligent innovations, business process improvement, and IT landscape transformation, without any upfront capital investment in infrastructure, database, hardware, etc. Moreover, it comes with pervasive data modelling capabilities and simplified deployment roadmap options.
Cloud adoption for SAP S/4HANA
Powered with Cloud and Analytics, SAP S/4HANA is undoubtedly a comprehensive, intelligent business suite delivering to organizations, unique insights, and intelligence. However, moving to SAP S/4HANA is not as simple as it may seem initially. It is dependent on your insight and capability to fundamentally examine your business processes, infrastructure, and data. Furthermore, you need to reconsider your business objectives and project priorities to achieve seamless migration to Cloud and realize all its benefits.
To evaluate how SAP S/4HANA can benefit your organization, it is always sensible to assess the consumption and configuration of your existing SAP environment. Subsequently, you need to create a migration to Cloud roadmap for seamless technical deployment, depending on project specific requirements, strategic transformation goals, etc.
Irrespective of the approach you choose, be it New Implementation or System Conversion, there are various advisory tools, such as Business Scenario Recommendations, Readiness Check Tool, etc. that can help you gain the necessary insight and confidence to simplify your move to SAP S/4HANA. After gaining clarity, you should continue forward with your S/4HANA adoption on Cloud in a phase-driven manner.
Five phases of successful SAP S/4HANA Cloud journey

Re-evaluate your current stage and develop a vision:
Before you start your Cloud journey, answer the reasons behind it. You need to evaluate your current IT landscape, analyze your business strategy, consider cross-functional dependencies, and develop a strategic vision before moving to SAP S/4HANA. Herein, Business Scenario Recommendations (BSR) for SAP S/4HANA can help you generate a comprehensive report on how your current system would be impacted and how you should prepare adeptly to derive true value propositions.

Explore the value of SAP S/4HANA:
Once you have evaluated your business landscape, you must start exploring all the value propositions of SAP S/4HANA that can help you transform the overall IT landscape and improve business processes. Mapping key business functions is yet another major area you need to consider while analyzing the values of SAP S/4HANA. SAP Innovation & Optimization Pathfinder can help you analyze all the business improvement opportunities. It also provides rich analysis of innovation recommendations, innovation acceleration, and IT optimization.

Future State Design:
During this phase, you need to start focusing on the technical aspects of your migrating specific parts of your IT landscape or processes to SAP S/4HANA. It is always advisable to define processes and IT landscape that you think are suitable for SAP S/4HANA in order to devise a future-ready migration layout. During this phase, organizations count on different tools such as Readiness Check and Maintenance Planner. Readiness Check highlights the required solution adjustments that are needed for system conversion. Maintenance Planner generates the stack file online from SAP marketplace, which is required to download the SAP S/4HANA software.

Migration and roadmap:
Before the transition begins, you need to outline clearly defined migration strategies to identify, evaluate and select the best migration scenario. To attain seamless transformation and successful SAP S/4HANA migration, you must define the strategy that best suits your vision depending on your current IT stage.

Plan S/4HANA Implementation:
The actual transition begins in this phase, and you must embrace a high-level project management approach to successfully migrate to SAP S/4HANA. As majority of organizations lack technical skill, competence, and expertise to implement such a project, it makes good business sense to collaborate with an expert.
Why Sify for SAP migration, infrastructure, and management?
It is important not to get overwhelmed by the adoption complexity, as finding the right partner will alleviate most of your concerns. Sify has a rich experience and all the state-of-the-art tools required for successfully migrating heterogeneous or homogeneous SAP workloads and managing them.
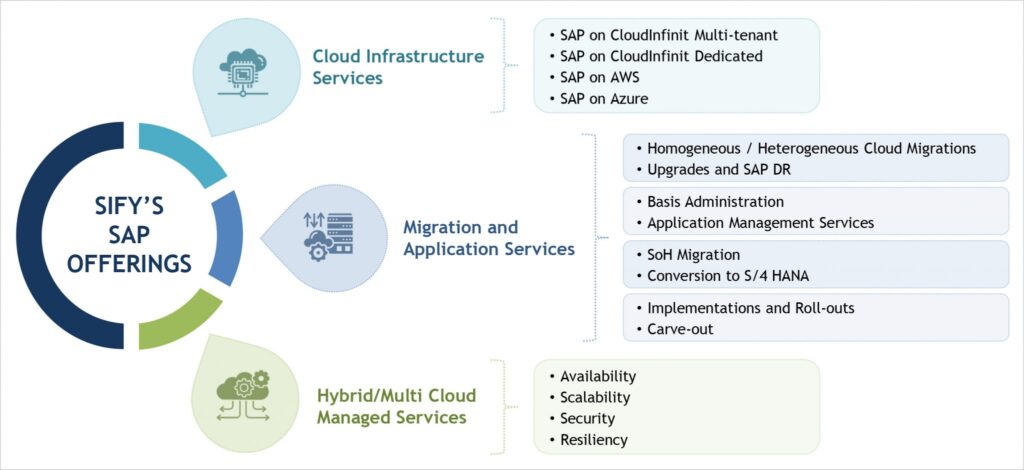
Sify provides you the option of choosing the most appropriate environment for your SAP workloads. You can host your SAP workloads on HANA grid (which is certified by SAP) on Sify’s proprietary Cloud – CloudInfinit. You also have the choice of deploying it on a Hyperscaler (AWS, Azure, etc.) with DR on Sify’s SAP grid or vice versa to leverage the benefits of Hybrid Cloud. Furthermore, we hold a distinct level of specialization in ECC to S/4HANA conversions, implementation and carve out scenarios. Sify’s integrated play across Network, Cloud and SAP ensures that you get flexibility, agility, and choice for comprehensive coverage of all your SAP needs.
Snapshot of Sify’s SAP offerings
Migration to Oracle Cloud: common pitfalls and best practices
Count on Sify to accomplish your migration goals
Enterprises worldwide are in a quest to leverage the true potential of the Cloud. As Cloud allows organizations to unify disparate business functions, streamline processes, enhance organizational efficiency, achieve resilience, and control cost, decision-makers across the business world are looking for the most suitable Cloud and a competent Cloud partner.
Herein, Oracle Cloud has certainly been able to garner attention by helping organizations optimize IT infrastructure, achieve operational excellence, and reduce cost significantly. Oracle ensures a very unique value proposition as it uses the same on-premises products and tools for Cloud. It is built from on-prem deployments, unlike other Cloud providers which started with a Cloud-native approach only. As organizations transition their processes, business functions, or implement a complete transformation to the Cloud, the “integration” between different Cloud and on-premise enterprise applications will be the focus. We know that not all enterprise applications will migrate to the Cloud at the same time, therefore it is imperative that existing on-premise integration is utilized to communicate between the on-premise applications and the Cloud applications via a common cloud integration platform. In such a situation, Oracle certainly ensures distinct advantages.
Oracle is the only cloud provider to offer guaranteed availability, management, and performance SLAs. Moreover, it also ensures greater control and visibility of Cloud resources, which further helps in improving top-line business performance. That’s why organizations are keen to migrate to Oracle Cloud.
However, organizations face distinct challenges and complications while executing the migration plan. As we work with organizations (across verticals) for their Cloud transition or migration projects, we have gained expertise in helping them identify all pitfalls and follow a trusted approach to create and implement successful migration to Oracle Cloud.
This blog highlights the major challenges faced by organizations during their migration journey to Oracle Cloud and the best practices to tackle those challenges. Furthermore, we shall discuss how Oracle Cloud, Sify’s hybrid IT-ready data centers (with Cloud Adjacent and Near Cloud data centers), and Network Services can help you accomplish your Cloud transformation goals competently.
 |
CHALLENGE: Not every workload is Cloud-ready for Lift-N-Shift |
 |
BEST PRACTICE: De-couple the workloads into different categories |
It’s a well-known fact that not all workloads can be migrated to Cloud using the same migration strategies. Therefore, Sify has come up with a comprehensive range of Cloud Assessment Services which help you decouple the workloads into two broad categories – the workload that must be migrated to Oracle Cloud and the workloads that can be hosted in Sify’s Hybrid IT-ready DC. This will help you draft the most appropriate and cost-effective Cloud adoption/migration plan.
 |
CHALLENGE: Inter-dependency between applications |
 |
BEST PRACTICE: Build migration specific business case for each application |
Sify’s Cloud Assessment and Migration Services help you identify inter-dependency between applications and build migration specific business case considering each application. Our Hybrid IT-ready data centers allow you to establish fast and secure interconnection among all your applications hosted in Oracle Cloud, without any network latency issue.
 |
CHALLENGE: How to deal with legacy applications |
 |
BEST PRACTICE: Leverage Cloud Integration Platforms for hybrid deployments |
As all enterprise applications cannot be migrated to Cloud due to architectures, dependencies, and cost, there needs to be effective integration between legacy and cloud applications. Sify is uniquely positioned not just with the ability to meet Network SLAs but also with the ability to design, implement and manage hybrid deployments with legacy on-premise applications and the Cloud applications, via a common Cloud integration platform leveraging Oracle technologies.
Count on Sify for a successful migration to Oracle Cloud
Sify complements Oracle’s public Cloud portfolio with its expansive service portfolio encompassing data center services, migration and assessment services, telecom, and managed services. This offers customers a holistic value proposition for their Cloud journey which no other service provider can offer.
With the Oracle Cloud data center co-located with us, Sify is in a unique position to offer customers the advantages of Oracle public Cloud and co-location of partial workloads from the same premises which are interconnected through a high speed, low latency, and highly secure ‘FastConnect’ link. This allows customers to go for their own hybrid data centers without having to worry about latency issues.
With our cloud@core strategy, Hybrid IT-ready Data Centers and Network Services offering <1ms latency for Hybrid deployments, we are the only Cloud Transformation partner that can help you leverage the true potential of hybrid Cloud. Our Hyperscale Cloud and Data Center Services, low latency, high bandwidth, and secure connections to Oracle Cloud ensure better performance at predictable costs. Moreover, our team of competent Cloud experts and Oracle-certified solution architects are willing to offer prescriptive guidance at every stage of your Cloud adoption and transformation, to help you achieve your Oracle migration goals.
Consolidate your Network with Sify
Rationalize, Scale, and Manage your network effortlessly.
In today’s technologically advanced era, enterprises across realms have complex ICT environments – virtual and geographically spread. The advent of Cloud and rise of multiple solution providers globally have encouraged organizations to pick and choose the perfect mix to host their applications, servers, and data across a diverse landscape of Data Centers and multiple clouds. This has benefitted organizations worldwide, in terms of ease of operations, higher level of flexibility and better speed to market. However, at the same time, one must acknowledge that management of such a highly complex ICT environment has become a major challenge for many organizations in the digital era.
Organizations must understand that all the components of their diverse IT and network infrastructure – consisting of applications, servers, machines, network peripheral equipment, sensors, or even distinct Cloud environments – are not discrete or isolated units anymore, but a part of a larger organization context, making them extremely valuable for business progression and business continuity. All these components must be unified and viewed in a consolidated way for better performance and security. That’s where, Network Consolidation becomes imperative!
Organizations that have complex ICT environments face distinct challenges that hamper their overall performance and efficiency. Some of the most common challenges in this changing and ever evolving Network and IT environment are:
- Multiple service providers management: Modern enterprises leverage a perfect blend of best-of-breed network solutions from distinct service providers as this ensures advantages of redundancy, resiliency, choice of network media, and connectivity to remote locations. However, managing all the distinct service providers is quite a challenging task and has some inherent problems, such as lack of ownership and visibility, inconsistency in services, inability to leverage analytics, and governance related risks.
- Limited in-house network management capabilities: This is another major concern for organizations across industry verticals. If they opt for establishing an in-house network management setup, then it becomes a very cost-intensive decision to hire the skilled workforce, procure the technology, develop the competence, and achieve a high level of scalability. Furthermore, an in-house setup would need hefty and timely investments to keep pace with evolving technology landscape.
- The demand for constantly re-architecting network: Every enterprise network nowadays has a host of different applications, which has given rise to changed traffic patterns. These mission-critical applications demand uninterrupted collaboration and traffic exchange, which calls for a continuous re-architecting of network to connect data, applications, people, and varied components of the IT infrastructure.
- Shift of focus from Network uptime to Application performance: Traditionally, network has always been uptime-focused, however in current situation where applications are hosted in multiple of Data Centers, Public & Pvt Clouds, businesses are more concerned about how applications perform over the network as this directly impacts the end user experience. The changing demands of high-performance computing and fast cloud migrations have led to a change in paradigm for networks with their SLAs being evaluated on Application intent rather than Network intent. Therefore, new-age networks must capably meet the rising needs of all mission-critical applications that are running concurrently.
- Unification of underlay and overlay networks: To meet changing demands of businesses, networks have grown and evolved organically over different periods of time. This has resulted in complex architectures of underlay & overlay networks. With changing priorities of organizations and rise of application-focused networks, it is important to unify the underlay and overlay networks for optimal utilization, enhanced efficiency, improved user experience, and robust security.
- Connectivity across DC and Cloud landscape: With increased Cloud adoption, it is very important to maintain a perfect sync between data centers and Cloud. Therefore, they need an excellent Network Interconnection that can guarantee seamless connectivity across all the data centers, Cloud environments, international cable landing stations, third party telco infrastructure, etc. for deterministic connectivity and extensive reach.
- Integration of IT, OT, and People: Majority of organizations nowadays have geographically distributed offices, where employees and end users use multiple devices in different regions. It is important to allow them secure and fast access to applications in Cloud and data centers for better experience, collaboration, and organizational efficiency. At the same time, the same Network must ensure seamless connectivity of IT Infrastructure as well as OT assets like WiFi access points, IoT devices and sensors. Herein, network plays an important role in integration of all aspects of IT, OT, and people.
As discussed above, organizations with complex ICT environments face distinct challenges. This not only hampers efficiency and performance but also impacts end user experience, hence compelling organizations to revisit their network strategies. Enterprises want actionable information to be available to end users wherever they are. The rise in mobility and multitude of devices has paved way for direct access to corporate information, which highlights the need of secure and consolidated network which can be scaled rapidly on-demand. The CIOs need to have complete visibility of all network assets and take decisions on network performance and network behavior dynamically. This can be achieved only through network consolidation.
Consolidating your network under one trusted service provider will ensure you a centralized real-time visibility and control over your entire network. Network consolidation improves network performance management and makes network provisioning easier with lesser handoff points between providers, devices, and IT assets, at a reduced cost!
Network consolidation becomes a very complex task and it has a lot of parameters and moving parts to be looked into. Therefore, it is imperative to seek an expert guidance in this quest.
Sify can help you accomplish your Network Consolidation goals. Some of the key differentiators that make us the preferred network consolidation partner are:
- Hybrid Network Strategy – Use of Internet for Business Applications: The shift from data centers towards Cloud has resulted in more prevalent use of the Internet as a connectivity option, in addition to MPLS. Today, an SLA-defined Internet strategy is a more reliable and pervasive way to establish a robust connectivity throughout the widely spread ICT environment. Hence, modern day businesses need hybrid WAN strategy – use of internet for business applications along with MPLS. Sify is empowered with India’s largest MPLS Network covering 1,600 towns and cities across India with 3,100 Points of Presence. We provide consistent, secure, high-speed Internet connectivity in more than 130 countries together with 800+ local and global partners. With our robust MPLS and Internet services, we can help you consolidate your network for both primary and secondary connectivity needs.
- Cloud Ready Networks – Advantage Hyper-scale: As majority of modern enterprises opt for hybrid or multi-cloud model, enterprises need ubiquitous connectivity to data centers and public Clouds. Sify’s robust interconnection network helps enterprises connect and integrate with Hyper-scalers seamlessly to simplify Cloud connectivity and reduce provisioning time. Our interconnection network improves cross-cloud application interaction, performance, and scalability, which ultimately paves way for enhanced quality of experience. Sify enjoys a great stature in the India Cloud market as we are the preferred partner of all major Hyper-scalers such as AWS, Azure, Oracle, and GCP including their respective Cloud connect services. With our Cloud connect, DC Interconnects and carrier neutral network with multiple internet exchanges, we deliver a well-architected and cost-effective Cloud-ready network for a secure, low latency and deterministic connectivity.
- Strategic Move from Wireless to Wireline Connectivity Media – More relevant than ever: Today, convergence of wireless and wireline is happening at a lightening pace. Till now, fiber penetration was restricted to backbone networks in the network value chain; however, as we move to the hyper-connected era, networks fiberization becomes important for the increasing cloud adoption. Therefore, Sify has invested in dense fiberization in backhaul and last mile connectivity. Sify’s state of the art 100G ethernet infrastructure – Metro-XConnect integrates multiple Clouds, our Cloud-adjacent data centers, third party data centers, and transit points in the Network. Our investments into Metro-XConnect can help customers consolidate their networks and leverage multiple benefits of Cloud, such as low latency, high reliability, improved scalability, and uninterrupted operations.
- Strong Managed Services and Network Operations Outsourcing capabilities: Empowered with strong Managed Services and Network Operations Outsourcing capabilities, Sify can help you integrate, consolidate, and transform your networks across varied ICT environments for visibility, control, and easy orchestration. Our integrated skillsets, processes, toolsets as well as the state-of-the-art Network Operations Center (NOC) and Security Operations Centre (SOC) can enable you to monitor and manage network and security devices comprehensively. Our NOC services are SLA-driven and outcome-based, which ensures predictable performance. Sify also helps in assessing & consolidating WAN networks; redesigning & reengineering as-is WAN network; and managing Network and Network assets 24X7. Additionally, you can outsource your Network operations and management, including management of all service providers and vendors.
- Integrated capabilities across Core, Management Layer, and Edge : In the digital age, enterprises need to focus on faster compute and Edge connectivity. To accomplish this goal, it is important to transform and rearchitect your network – at the core, the management & visibility layer, and the Edge. With our DC and Cloud Interconnects, combined with expertise to deploy technologies like SDWAN and NFV, we hold expertise in network transformation at the core. At the Network Management layer, Sify can manage your WAN, provide 24×7 monitoring of links, undertake network management under a unified SLA across multiple service providers. At the Edge, Sify ensures end to end implementation and access configuration of Wi-Fi, IoT devices and integration with the Enterprise Network.
AWS Cloud Cost Optimization
AWS cost optimization is an ongoing process. AWS cloud resource utilization needs to be continually monitored to determine when the resources are being under-utilized or not being utilized or idling to reduce the costs by deleting/terminating/freeing the unused resources.
It’s also helpful to consider the Saving Plan or Reserved Instances to ensure full utilization as per the anticipated constant level of consumption.
While the fundamental process of cost optimization on AWS remains the same – monitor AWS costs and usage, there are a number of tactical ways to analyze the operational data to find the opportunities for savings and take actions to realize the savings.
Pillars of Cloud Cost Optimization
1. Right-Sizing
Identify the resources with low-utilization and reduce the cost by stopping or rightsizing.
- Use AWS Cost Explorer Resource Optimization report to get the list of idle or low utilized resources. Reduce the costs by either stopping or downsizing the instances.
- Use AWS Compute Optimizer for downsizing recommendations within or across instance families, upsizing recommendations to remove performance bottlenecks and recommendations for EC2 instances that are parts of an Auto Scaling group.
- Identify Amazon RDS, Amazon Redshift instances with low utilization and reduce the cost by stopping (RDS) and pausing Redshift outside of business hours or non-processing timeframe.
- Use Amazon EC2 Spot Instances to reduce EC2 costs where possible – SPOT instance mgmt. can be effectively managed by 3rd part tool, such as Spotinst, for automatic termination and new instance availability without impacting end users.
- Review and modify EC2 Auto-Scaling Groups configuration to ensure scaling is happening on the right thresholds instead of setting it at the lower thresholds.
- Try using Elastic Kubernetes Services (EKS) and Elastic Compute services (ECS – EC2 Model) worker nodes under auto-scaling using SPOT instances (instead of on-demand/RI) for reducing the cost.
- Consider using Elastic Compute services (ECS -Fargate) to start the tasks with lower configuration (e.g. 0.5 vCPUs & 1GB RAM) per task and use auto-scaling instead of higher configuration per task.
- Multi-AZs configuration for DEV, test, UAT, or DR environment may not be necessary or useful for RDS, Redis, NAT, or other PAAS services (unless business really requires achieving any objective); therefore, it’s important to design wisely.
2. Instance Family Refresh
Each instance/series/family offers different varieties of computing, memory, and storage parameters. Instance types within their set groupings are often retired as a unit when the hardware required to keep them running is replaced by newer technology.
- Upgrade instances to the latest generation offering lower costs.
- For PAAS services, such as RDS, Redis, ElasticSearch, MSK, use instance type wisely, particularly for pre-PROD or DR and appropriate AZs to scale the instances. It may not require more than 2 AZs even while considering business SLAs. Keep an eye on the latest family of infrastructure and refresh to take the benefits of lower costing.
- Use low costing instance type for Development, QA, or the environment (e.g. T3a) wherein performance benchmarking certainly is not required for the business SLA.
- Always start with low and upgrade the right size to a suitable family considering the business use cases and traffic patterns.
3. Compute Savings Plans to reduce EC2, Fargate and Lambda costs
Compute Savings (Compute Savings Plans and EC2 Instance Savings Plans) Plans automatically apply to EC2 instance usage regardless of instance family, size, AZ, region, OS or tenancy, and apply to Fargate and Lambda usage. Use one year, no upfront Compute Savings Plans to get a discount of up to 54% compared to On-Demand pricing. Once you sign up for Savings Plans, your computer usage is automatically charged at the discounted Savings Plans prices. Any usage beyond your commitment will be charged at regular On-Demand rates. Please follow Point Nos. 1 and 2 before adopting Saving PLAN. Saving Plan has a lot of advantages over AWS Reserved Instances with one condition – “Usage commitment/Hour”
Reference link – https://aws.amazon.com/blogs/aws-cost-management/getting-started-with-aws-savings-plans/
4. Reserved Instances (RIs)
Even though the Saving plan supersedes the RI option, some of the PAAS services are outside of the Saving Plan program as of today in April 2020.
- Purchase reserved nodes for RDS, Redshift, Elasticsearch and ElastiCache Services to reduce the cost.
- Many instance type discounts are larger and at the top end may be over 60% in the case of some 3 year all upfront terms. Identify the instances & take call saving plan vs RI intelligently.
- You can get shorter term RIs on the marketplace.
5. Scheduling on/off times
It’s worth scheduling on/off for non-production instances used for development, staging, testing, and QA as it can save up to 65% of running these instances if you apply an “on” schedule of 8.00 a.m. to 8.00 p.m. from Monday to Friday. However, it’s possible to save a lot more — especially if development teams work in irregular patterns or irregular hours. Plan more aggressive schedules by analyzing utilization metrics to determine when the instances are most frequently used or apply an always-stopped schedule which can be interrupted when access to the instances is required.
6. Orphaned resources
Identifying waste takes time and accurate reporting. It is a great reason to invest time and energy in developing a proper tagging strategy to make this an easy process.
- For unutilized AWS EC2s, use Cost Explorer Compute Optimizer report or extract CW stats and take actions.
- Terminate VMs that were spun up for training or testing.
- Delete unattached EBS volumes – Check Volumes page and available EBS volumes status.
- Delete obsolete snapshots and lifecycle as required to meet the business demand.
- For idle load balancers, try to use ALB with path/content-based routing.
- Release unattached Elastic IP addresses.
7. Storage
- EBS volumes that have very low activity (less than 1 IOPS per day) over a period of 15 days indicate that they are probably not in use. Identify these volumes using the Trusted Advisor Underutilized Amazon EBS Volumes Check. To reduce costs, first, snapshot the volume (in case you need it later), and then delete these volumes.
- Use S3 Analytics to analyze storage access patterns on the object data set for 30 days or longer. It makes recommendations on where you can leverage S3 Infrequently Accessed (S3 IA) to reduce costs. You can automate the process of moving these objects into lower-cost storage tier using Life Cycle Policies. Alternately, you can also use S3 Intelligent-Tiering, which automatically analyzes and moves your objects to the appropriate storage tier.
- Move infrequently accessed data to lower-cost tiers.
- Use S3 One Zone if business SLA allows you to do so.
8. Containerization
Containers can help to get the most out of available computer hardware and software resources which are Lightweight, have start-up time in milliseconds, and require less memory space. Containers help to achieve the scale of the economy by reducing the IT management resources, snapshot size, spinning up applications, reduced & simplified security updates, etc. Containers are a better choice when your biggest priority is maximizing the number of applications running on a minimal number of servers.
9. Local Caching
If data transfer from EC2 to the public internet shows up as a significant cost, consider using Amazon CloudFront. Any image, video, or static web content can be cached at AWS edge locations worldwide, using the Amazon CloudFront Content Delivery Network (CDN). CloudFront eliminates the need to over-provision capacity in order to serve potential spikes in traffic. Use CloudFront when your userbase is geographically distributed.
10. VPC endpoints
Heavy data lifting to S3 from private subnets (e.g. static contents, backup, videos, etc.) require NAT gateway. Use VPC endpoint to reduce the NAT gateway data out the cost and move data securely over the AWS backbone. This will reduce the NAT Gateway data out the cost that occurs to S3.
11. Regional and AZs Cost
AWS AZ and regional cost can be eliminated wisely through right solutioning.
With-in availability zone (AZ)
- Data transfer costs for transferring data in the same region and within the same availability zone are zero, however with one requirement that you must be using a private IP address.
- If you are using a public or Elastic IPv4 address or IPv6 address, data transfer out from EC2 will be charged at 0.01/GB. In the same way, data transfer into AWS EC2 will be charged at 0.01/GB if you are using a public or Elastic IPv4 address or IPv6 address.
Across availability zones in the same region
- Data transfer between AWS services located in the same region but in different availability zones is considered as regional data transfer and is charged at $ 0.01/GB (outgoing data transfer).
- In the same way, data transfer into EC2 from an AWS service in another availability zone is charged at $ 0.01/GB.
This is only true for some AWS services like Amazon EC2, Amazon RDS, Amazon Redshift or Amazon ElastiCache instances, etc.
- Architect your systems so that there is minimal data transfer across AWS regions or availability zones.
- Architect your AWS environment such that data transfer is restricted to within an availability zone or within a region at the most.
- Try to use private IP addresses instead of public or elastic IP addresses wherever possible.
Conclusion
Fine-tuning your cloud infrastructure is critical to make sure that your overall bill stays in the limit. Proven cloud cost optimization strategies outlined in this blog will help you cut down your cloud costs by eliminating unused resources and/or choosing the right resource plan. Sify has been meticulously managing the cost optimization projects of large enterprise customers for many years to reduce their AWS bills substantially. Sify, with its highly dedicated, well experienced and AWS certified SMEs, can help you realize your business objectives by fine-tuning your environment.
If you are concerned about your ever-increasing AWS cost, the above-given strategies will help you optimize the cost. You can also choose Sify – the experienced AWS Managed Service provider – for yielding the best results.
Business use cases for high-performance computing
Emerging technologies such as IoT, Artificial Intelligence, and Machine Learning have not only changed the business dynamics but have been generating an exponential volume of data, posing difficulties in its management. Processing this exponential burst of data with varying workloads in a timely and cost-efficient manner requires modern systems like High Performance Computing (HPC). Despite being in its early adoption stage, HPC is quite promising, as it has the capability to solve emerging business problems. Many business use cases have been developed, capturing the attention of the enterprises across the globe. Some of these use-cases where HPC has helped enterprises solve their problems are discussed here.
Fraud detection in the financial industry
Financial frauds have rocked the world with their inventiveness and scale. Some high-profile frauds such as Ponzi schemes, misleading investment schemes, identity fraud, phishing, card fraud, counterfeiting, skimming, fake prizes, and inheritance scams have duped many unsuspecting investors or users. The Global Economic Crime and Fraud Survey conducted by PwC in 2018 reveals that 49% of the organizations faced an economic fraud in the previous two years. While 52% of these threats were internally born, 40% were from external sources.
With a centralized system of fraud detection, information can be gathered from all the available sources. This system can help detect and prevent cyber-attacks, improve data privacy, enhance data protection, and support the digital forensic investigation. Given the humongous volumes of data, the system that is installed must have the capability to detect anomalies and intrusion attempts. Legacy data centers, despite their high capacities, are incapable of handling such large volumes of data. In this scenario, High Performance Computing can prove to be a useful aid in modern fraud detection and risk modeling, thereby helping financial organizations detect attacks on their systems as they occur, preventing financial fraud. PayPal implemented an HPC environment, and within a year of its adoption, it was able to save $710 million that would have been stolen by cyber thieves.
Personalized healthcare and clinical research
Modern advancements in healthcare have helped in the development of many pharmaceutical drugs and in identifying treatment options for a variety of ailments. The adoption of information technology by physicians, surgeons, and other medical professionals has helped them deliver accurate and timely medical treatment to their patients. Advanced medical simulations are often employed to ascertain the positive and negative effects of medicines on a patient profile to determine the most effective treatment option. These simulations demand high computing power as a number of factors need to be taken into account. This is another area where High Performance Computing can come to the aid of medical professionals with its significant computational power. Medical professionals can drill down into patient information at the genomic level, using millions of data points to help diagnose and identify personalized treatments for the patient.
Large hospitals have been using HPC for research. TGen and NMTRC have together developed an HPC system to obtain insights in much faster time into cancer and pharmaceutical research. By using these systems, new drugs can also be discovered, and life-saving medical treatments can be identified and personalized.
Smart energy grids
Smart energy grids are deployed to reduce energy consumption and offer more flexibility and reliability than traditional grids. These grids help in supplying energy to millions of households by integrating multiple energy sources. In order to supply, optimize, and maintain energy efficiency for multiple cities and neighborhoods, a huge volume of data is captured from millions of devices, including individual meters and consumption devices. These devices can generate exabytes of data, for which enormous computing power is needed for processing. Traditional servers cannot fulfill this need. However, with HPC, a huge volume of data can be processed and analyzed with efficiency in real-time.
Manufacturing Excellence
Large manufacturing enterprises have already begun to make use of the power of HPC, which is used for IoT and Big Data analysis. Based on the analysis results, real-time adjustments are possible in processes and tools to ensure an improved design of a product, increased competitiveness, and faster lead times.
High Performance Computing is capable of running large simulations, rapid prototyping, redesigns, and demonstrations. An example could be a manufacturing unit that would improve its manufacturing flow with insights from the processing of 25,000 data points from customer intelligence. The first-ever autonomous shipping project of the world is making use of HPC computing, which involves processing a large amount of data collected from sensors. The data includes details of weather conditions, wave points, tidal data, and conditions of various systems installed.
High Performance Computing offers significant benefits over traditional computing for manufacturing enterprises. It can help an automobile unit vehicle maintenance. A wholesaler could optimize the supply chain as well as stock levels. HPC is also used in R&D. The innovative design of the 787 Dreamliner Aircraft by Boeing is a result of HPC-based modeling and simulation that helped the company conduct live tests on the aircraft to test the prototype.
HPC has become indispensable for enterprises to derive competitive advantage in the fast-growing business world and scaling technologies.
Sify Data Center and cloud services help you to centralize your IT infrastructure, operations, storage & management and enjoy tremendous scale and a lower cost of ownership. Our consultative solution approach helps you define a business technology strategy where delivery of services supports clear business outcomes.
How to plan a cost-effective Data Center transformation
Data Centers have become nerve centers of the organizations in the modern digital world. Their performance and efficiency are crucial levers of organizational success. The challenge for technology heads has been to arrive at Data Center solutions that are cost-effective, offering value without compromising on essential features. Utilizing available space for Data Center scaling is a cost-saving method often employed by organizations. This measure can only yield short-term value. Creating a cost-effective Data Center with optimum performance and decent ROI, in the long run, requires elaborate planning. Companies can plan a cost-effective Data Center transformation using the following measures.
Disaggregated architecture
We often visualize a Data Center like the one with racks of servers, blinking and humming away. What happens when one of the server modules get compromised or damaged? Will you replace the entire server? It will be wiser if you replace or upgrade only the equipment in question as this approach has lower downtime and is more cost-effective. A disaggregated architecture like High-Performance Compute (HPC) offers this benefit. An intelligent HPC architecture can transform your Data Center and give you significant savings in the long term.
The plan for a Data Center transformation or development relies on some key functions like design computing and power management. Making effective use of these functions would result in cost saving. Electronic design automation can shorten the design cycle for the Data Center architecture, which reduces the time to market. Further, with disaggregated architecture offered by HPC, physical operations become more cost-effective than workloads running on the cloud. A comparative cost saving upwards of 60% can be achieved.
Traditional Data Centers used power architectures with limitations and thus, incurred a major cost when scaling up, but modern Data Centers use low power consuming servers and efficient cooling systems and thus, have higher Power Usage Effectiveness and less cost. A desegregated architecture can further bring down the operating costs of a Data Center.
Micro-Data Centers
Scalability, speed and reliability. The modern business world relies on these elements for its operation, and they can be optimized by deploying the right technology. If the costs are not managed well, it can put a strain on the organization. The question is – Is the desired ROI achievable? The use of Micro-Data Centers that are located closer to the points of consumption can reduce latency and cost both for cloud and a remote Data Center. The micro-architecture can reduce up to 42% of the capital expenditure when compared to traditional Data Centers.
Data Centers designed with technologies like virtualization, compaction, and hyperconvergence result in significant cost savings. Virtualization allows a company to use the computing power across workloads in a Data Center, saving power; compaction consolidates multiple racks into one, saving space. On top of it, hyperconvergence integrates high performance compute, high performance storage, and networking, thereby increasing the speed of deployment.
Power provisioning
Around 3% of the total electricity in the world is utilized by global Data Centers, and that amounts to roughly 416 terawatts. By 2025, Data Centers would end up consuming a fifth of the global power. No wonder, power is a major concern when it comes to Data Centers, and power-saving measures bring cost benefits for an organization. Power provisioning can be used to optimize Data Center power consumption by understanding how power is consumed by equipment, servers, and workloads, and optimizing it.
Power supplies have a sweet spot, the level at which high operational efficiencies can be achieved. However, most Data Centers operate below this level. The reason why companies could be restrictive in using enough power is the cautious measure of average and peak power consumption given on the nameplate of a power supply equipment. However, it is important to understand that if the Data Center is operating below this sweet spot, it could be wasting energy, and this wasted energy would further increase the need for cooling. Using the right power supplies, amortizing power across servers, and running Data Centers at optimum loads can bring efficiency and cost-savings.
A cost-effective Data Center transformation can be achieved through effective architecture, fast deployment, and optimized power consumption. Organizations can beneficially employ these measures when scaling up their Data Centers for achieving long-term gains.
Sify Data Center and cloud services help you to centralize your IT infrastructure, operations, storage & management and enjoy tremendous scale and a lower cost of ownership. Our consultative solution approach helps you define a business technology strategy where delivery of services supports clear business outcomes.
How to orchestrate and manage workloads in multi-cloud environments
Multiple business applications of an enterprise are usually housed on-premise and on-cloud infrastructure. In a multi-cloud environment, multiple cloud providers build the IT portfolio, which would mean that the company must manage multiple service level agreements. Technically, this environment provides the enterprise with a workload migration capability between different cloud services on demand, depending upon which is beneficial.
However, if the integration of IT systems on a multi-cloud environment are not tightly coupled, it may lead to various issues. In a hybrid environment, clouds can be interconnected, but in a multi-cloud environment, alternative measures must be taken as there are multiple service providers. Integration and orchestration are the standard measures employed to manage workloads in a multi-cloud environment.
A multi-cloud is not a hybrid cloud
A hybrid cloud would have different models for deployments in public and private clouds, but a multi-cloud environment would have multiple service providers who may be delivering services using the same type of deployment. At an advanced level, the tapestry of a multi-cloud system can contain categories of private cloud, hosted private, hyperscale cloud, and hybrid clouds with each having multiple vendors.
Multi-cloud management is challenging as different clouds may not be interconnected as in a hybrid cloud. This adds complexity to the management of resources, capacities, services, compliances, and finances. For governing resources in a multi-cloud, automation tools are often used. On top of it, orchestration can help streamline the functions of these tools. However, using multiple tools for managing different domains can still be complicated. Deploying automation technologies that can work across environments and help manage assets throughout may be beneficial. This can reduce complexity, enhance performance and strengthen the security of the multi-cloud system.
For the system to be agile and to maximize the value of a multi-cloud system, the workloads on the cloud should be properly mapped to specific types of clouds. This makes orchestration and management of workloads across multiple clouds easier in an integrated system. With this strategy in place, the user need not jump between different provisions while orchestrating between different workloads. Moreover, integration enables a combined visibility of all resources such that their costs, logs, metrices, and performance indicators, can be accessed through single interface in real time.
Managing a multi-cloud system
A standard way to approach multi-cloud management would be to create a blueprint for integration and management, in which strategies can be designed for ITSM integration, database monitoring, business process analysis, patch management, and life cycle management. An example of a strategy would be the standardization of resource consumption. A company can standardize the consumption patterns of resources based on the type of cloud and the service provider. For instance, one service provider may be used only for data analytics while others would serve the storage necessities, and a third would be used to work for Artificial intelligence applications.
To be able to manage this multi-cloud environment efficiently, a company needs to have an integrated system of resources. Integration makes it possible to monitor all the available resources, which is essential for the effective functioning of a multi-cloud system. Monitoring enables visibility into cloud networks, specific applications, and even potential threats faced by components of the cloud infrastructure.
Companies cannot take a traditional approach to manage the multi-cloud systems because unlike the earlier environments; resources are not homogenous in a multi-cloud environment. A managed multi-cloud in silos with individual tools can be both difficult and costly. Agility and flexibility of a multi-cloud system cannot be ensured if the complexity persists. Integration can help address such issues by making a multi-cloud system appear like a single system.
For effective management, the integration should be carried out along six dimensions: organization, business, processes, governance, information, and tools. After integration, an IT administrator can use a single interface to access all resources and take required actions for managing them.
Specific applications can be bundled within containers for the ease of maintenance. This packaging also increases the portability of applications as they separate the applications from their runtime environments. The apps within a container can easily be moved between cloud services while retaining their functionality. Based on individual criteria such as cost, availability, and storage space, the organization can freely select a cloud service provider. Containers are particularly ideal for a microservices environment in which software is built in such a way that the applications are broken down into very small components that are easily portable.
A managed multi-cloud service-based environment can always provide agility and a higher level of flexibility when compared to traditional approaches. Orchestration and integration are the keys to successful management of a multi-cloud environment. Orchestration can streamline automation, reduce complexities, enhance performance, and improve security. With integration comes visibility while containerization enables portability and easy maintenance.
Sify’s many enterprise-class cloud services deliver massive scale and geographic reach with minimum investment. We help design the right solution to fit your needs and budget, with ready-to-use compute, storage and network resources to host your applications on a public, private or hybrid multi-tenant cloud infrastructure.
Future of Data Center: Architectural Advances
Data is growing at an exponential rate in the modern borderless world. Over 2.5 Quintilian bytes of data is generated every day across the globe. India alone is set to produce 2.3 million petabytes of digital data by the year 2020, and it is growing at a rate that’s much faster than the world average. Many enterprises are also exploring online data backup in the cloud further fueling this data explosion.
This data explosion increases the demand for storage capacities that are served by Data Centers. In just two decades, Data Centers have scaled up from the size of a room to the size of a commercial tower giving way to accommodate this increased storage need. Besides storage, modern Data Centers are also sprucing up to handle more services. They are more connected than ever and can meet the needs of the contemporary business world. New solutions have emerged around Data Center architecture that can bring competitive advantages to users through more optimized performance. Data Centers have now become critical components of a modern IT infrastructure.
In India, we see emerging businesses growing at a fast pace, with cloud computing technologies and cloud warehouses taking the lead to store enormous amounts of digital data. At the beginning of the 21st century, most organizations in India had captive Data Centers that were self-managed. With advances introduced in cloud technologies and specialized players adding more capabilities, the self-managed option was replaced by the outsourcing model. Increase in the users, economic growth of the country, and cost advantages of cloud-based Data Centers are some of the trends driving adoption of a cloud-based architecture. Captive Data Centers are expensive to accommodate and challenging to scale. However, cloud-based Data Center architectures are more flexible.
Many new technologies, services, and facilities that were premium and rare earlier are now part of standard offerings in modern Data Centers. These services are reshaping the way businesses operate today.
Another trend to note is the emergence of Modular 4th generation Data Centers. These Data Centers comprise modular units that help in quickly scaling up the infrastructure. In addition to the components in the racks being modular, the building itself could be modular. For instance, some Data Centers are built in shipping containers. Scaling up means adding more shipping containers with Data Center units.
Resolving the Challenges
Many challenges of the past have now been resolved with architectural advances in the Data Center space. For instance, Pod architecture for SaaS assigns a set of machines to a specific job or customer for all of its required tasks. To create redundancies for power and cooling in a Data Center, a lot of assembling needs to be done which can incur a cost. You may also need to construct additional racks. However, POD comes with frames that are free standing and compatible with most equipment so it can be used for all needs including power, cooling, and cabling. So, your need for construction within the Data Center facility is minimized. It can simplify infrastructure scaling to support your digital growth. It is a standardized deployment that can automate user provisions. It allows you to use shared storage, firewall, and load balancing while customizing individual PODs as per your business needs. When scaling up users, you would not need to perk up your whole infrastructure but only add or remove specific resources user-by-user, which can help reduce overheads.
While Data Centers serve as an ideal place to use your critical applications, operating them has been a big challenge in the past. A Data Center is affected by many environmental factors that add inevitable complexities. A Data Center operator needs to take care of the cooling needs of Data Centers as well as maintain correct levels of air and humidity in the storage spaces. These challenges make it worthwhile for companies to try cloud-based shared storage space managed by third-party experts who could be better equipped to counter these problems. In modern warehouses, Computer Room Air Conditioning (CRAC) device is used instead of traditional air conditioning, which can monitor as well as maintain humidity, air flow, and temperature in a Data Center.
The future is smart!
The future of the Data Center is smart: modern Data Centers are now offering converged infrastructure, and the trend is further moving towards hyper-convergence. This has brought many advantages for Data Center operations and has also solved problems that paralyzed companies earlier. The risk of hardware failure, for instance, plagues companies with the risk of losing data and they struggle to rebuild their infrastructure. Siloed approaches to managing servers was another challenge that made Data Center operations expensive and complicated. With converged infrastructures, the process of managing a Data Center gets organized; with a single interface used for infrastructure management, your company turns more proactive in streamlining your operational processes and in keeping your data on the cloud safe.
While consolidation of operations through convergence makes management easier, most servers are still siloed, and that is where hyper-convergence plays its magic. Hyper-converged Data Centers are software-defined Data Centers that are also called smart Data Centers. They use virtualization and converge all operational layers including computing, networking, and storage into a single box. With hyper-convergence, everything is now on the same server which brings improved efficiencies, reduced costs, and increased control over Data Center components.
Colocation: A trend to watch
Rethink IT, replace captive servers with cloud services. You would now need much less space for storing the same amount of data than you needed in a captive Data Center. Welcome to the concept of managed colocation!
Colocation services (or Colo) are delivered by Data Center solution providers to enhance user experience. A hybrid cloud drives them and provides specialized services for their users. A collocation is a place where customers have better control over their private infrastructure, and with increased proximity to the public cloud, they can also be closer to their customers.
A colocation service relies on the principles of abstraction, software-based provisioning, automation, unified management, and microservices. Colo facilities are highly flexible as it can reap the advantages of both private and public cloud with a hybrid infrastructure. While private cloud gives enhanced security and control, the public cloud makes it easy to transport data over encrypted connections and gives you additional storage space.
Modern colocation services are now shifting to Data Center-as-a-Service (DCaaS) which is a much more flexible deployment than Software as a Service, Platform as a Service, and Infrastructure as a Service models. A hybrid DCaaS colocation architecture has a public IaaS platform, on hosted or on-premise private cloud and a Wide Area Network (WAN) to connect the two. A major advantage of DCaaS is the change in the cost equation. DCaaS providers have high economies of scale that allow them to offer you volume-based discounts taking your costs down. The DCaaS hybrid cloud architecture not only provides hybrid storage flexibility and cost advantage but also other benefits like increased redundancies, improved agility, and maximum security.
A hybrid cloud combines the resources available to you on the private cloud and the public cloud and gives you the flexibility to seamlessly move your data between them. With changes in your cost structures and business needs, you can flip your resources between the two clouds anytime. If you’ve reached the designed capacity of your current private cloud, you can always switch to a Public cloud for further expansion. For instance, Cloud bursting can give you on-demand storage over the public cloud so that you can shift the increased burden on your private cloud to the public in peak business seasons.
Data Center technologies are still emerging, and new architectures like hybrid cloud and hyper-convergence are taking shape. In the future, more companies would realize the benefits of these architectural modifications and will be able to enjoy far higher capacities and advanced Data Center management capabilities.
Sify offers state of the art Data Centers to ensure the highest levels of availability, security, and connectivity for your IT infra. Our Data Centers are strategically located in different seismic zones across India, with highly redundant power and cooling systems that meet and even exceed the industry’s highest standards.