How to Measure Return on Investment from a Learning Program
Now more than ever, return on investment (ROI) is vital to businesses of all sizes. Firstly, you must accurately calculate the ROI you will achieve from a project to gain approval. Then, ROI needs to be measured to demonstrate you have met or exceeded your goals.
ROI within a business case must be aligned with monetary values as much as possible. To gain approval for a learning program, the business wants to know what financial gains there will be.
Challenges of measuring ROI
For learning and development teams, predicting and measuring ROI is difficult. Understandably, ROI is aligned with financial gain for the business. And although the benefits of learning and development are clear, aligning them to a monetary value is complicated. Moreover, a learning program can contribute to the business indirectly or the true benefits can accrue over the long term. These factors mean that getting significant investment for new learning and development programs is complex.
How to measure ROI
As we have established, businesses want to see a monetary ROI value to justify learning and development spend. Once implemented, continued ROI measurement and reporting are vital for continued investment.
The challenge is every learning program is different, so it is difficult to use an ROI tool that fits all scenarios.
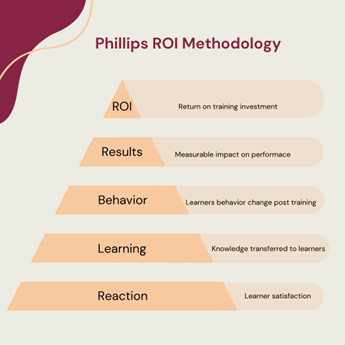
That said, there is certainly room in your ROI calculations for the best-known tool in the industry, the Phillips ROI Model.
Phillips developed his methodology in the 2000s, which builds on the original Kirkpatrick Model, which was developed in the 1950s, to include ROI. It compares the program’s total cost to its total monetary benefits, calculated as a cost/benefit ratio.
To achieve this, you need to isolate the training benefits and eliminate any non-training factors that may have contributed to the business impact. For example, competitive environment and seasonal effects that temporarily contribute to business improvements.
Calculating Return on Investment
Phillips ROI calculation is:
ROI = (Total Program Benefits – Total Program Costs ROI/Total Program Costs) x 100%
For example, let us assume that we are going to measure the effectiveness of a training program on health and safety for 50 people. We know that because of the program, the number of accidents has been reduced by 20 throughout the year. This has directly increased the company’s revenue by £100,000 per year. The total cost of the program was £50,000.
So, the benefit-cost ratio (BCR) is: £100,000/£50,000 = 2. In other words, for each £1 spent on the training program, £2 is returned.
Using the Phillips ROI calculation, the ROI of the program is calculated as so:
(£100,000 – £50,000/£90,000) x 100% = 55%
This means that every £1 spent on the program is returned and an additional £0.55 is returned as a profit.
Read the in-depth guide to Phillips ROI Model
Assigning Monetary Values to Tangible Learning Outcomes
It is easy to do an ROI calculation with sample numbers for an abstract example but in practice, it is a complex exercise to put monetary values on learning outcomes. Unfortunately, to build a successful business case and a successful learning program it is crucial you get an accurate ROI. That means selecting metrics that will accurately show the benefits of your program.
Hard data that can be converted easier include:
- Additional sales: Profit from these sales
- Employee time savings: Cost of the saved time calculated based on the average rate per hour
- Reduction of equipment downtime: Can be calculated in comparison with the results of the past periods
- Reduction of employee turnover: Money that you save on recruitment and onboarding
- Quality improvement: Money that was saved thanks to reducing the number of defective items
- Reduced costs: Online courses eliminate travel expenses and the time it takes to travel to and from the learning venue.
Further Reading: The Bottomline on ROI, Patricia Pulliam Phillips
Identifying and Reporting on the Intangible Benefits
Whilst every effort should be made to assign a monetary value to as many learning outcomes as possible, sometimes it cannot be done. Most learning programs will have intangible benefits that fall into this category. For example, finding metrics to demonstrate how your learning program has improved the public image of your organisation or how it enhanced the company culture is difficult.
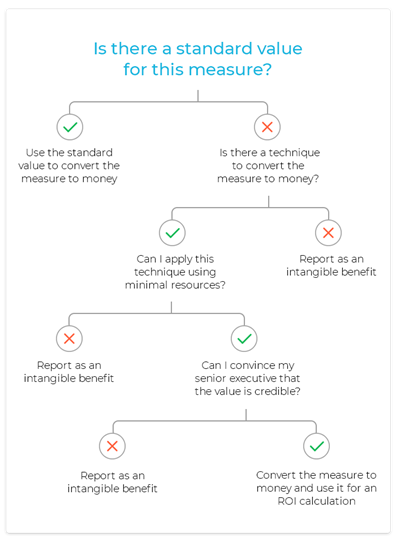
The challenge is this soft data is subjective so even with the best intentions, the data is often inaccurate and not credible.
If in any doubt, the ROI Institute offers some guidance:
The Impact of Digital Learning
The rise of digital learning, or e-learning, as part of a fully online learning program or a blended learning approach makes calculating ROI an easier task. Digital learning programs run through a Learning Management System (LMS) so you can document, track, report, automate and deliver your training program online.
Another consideration is learning content, when done well, can be used for years after the program launch. This long-term usage of learning content makes an ROI calculation more favourably than single-use learning content such as traditional classroom-based learning.
Creating a Blended Learning Platform to Reinforce Company Culture for a Global Media Giant
Summary
It is essential for any learning program to demonstrate value for the business with both tangible and intangible benefits. Predicting ROI to ensure the program is approved and then measuring and reporting ROI to establish it as part of your ongoing learning strategy is challenging but achievable with the right support and approach.
Digital learning via an LMS undoubtedly makes measuring and reporting hard data easier. It also means the system administrator has a wider choice of data to track and report on.
The global workforce is continually evolving. A multigenerational workforce and a shorter shelf life for knowledge have placed a premium on reskilling and upskilling. It means there is ever-increasing importance on attracting, nurturing, and retaining the best talent for your organisation.
The LMS offers your end users a centralised place for learning content to ensure seamless learning is accessible anytime and anywhere. Administrators can create personalised learning courses or learning journeys for individuals, teams or company-wide and track and report on progress using their choice of metrics.
How Sify Can Help
Sify Digital Learning is a specialist digital learning partner that offers the complete learning solution you need to attract, nurture, and retain the best business talent.
A successful learning program is an evolving journey because you are dealing with a constantly changing audience: your employees. Whether your goal is to boost employee productivity, reduce staff turnover or improve company culture or a combination of all three, Sify can help.
We provide the two fundamental components of a successful digital learning program: the LMS and the learning content it holds whether it is Off the Shelf and Custom content.
SAP Security – A Holistic View
With 90%+ of Fortune-500 organizations running SAP to manage their mission-critical business processes and considering the much-enhanced risk of cyber-security breach in today’s volatile and tech-savvy geo-socio-political world, security of your SAP systems deserves much more serious consideration than ever before.
The incidents like hacked websites, successful Denial-of-Service attacks, stolen user data like passwords, bank account number and other sensitive data are on the rise.
Taking a holistic view, this article captures possible ways, remediation to plug in all the possible gaps in various layers. (Right from Operating system level to network level to application level to Cloud and in between). The related SAP products/solutions and the best practices are also addressed in the context of security.
1. Protect your IT environment
Internet Transaction Server (ITS) Security
To make SAP system application available for safe access from a web browser, a middleware component called Internet Transaction Server (ITS) is used. The ITS architecture has many built-in security features.
Network Basics (SAP Router, Firewalls and Network Ports)
The basic security tools that SAP uses are Firewalls, Network Ports, SAP Router. SAP Web dispatcher and SAP Router are examples of application level gateways that can be used for filtering SAP network traffic.
Web-AS (Application Server) Security
SSL (Secure Socket Layer), is a standard security technology for establishing an encrypted link between a server and client. SSL authenticates the communication partners(server & client), by determining the variables of the encryption.
2. Operating System Security hardening for HANA
SAP pays high attention on the security topic. At least as important as the security of the HANA database is the security of the underlying Operating System. Many hacker attacks are targeted on the Operating System and not directly on the database. Once a hacker gained access and sufficient privileges, he can continue to attack the running database application.
Customized operating system security hardening for HANA include:
- Security hardening settings for HANA
- SUSE/RHEL firewall for HANA
- Minimal OS package selection (The fewer OS packages a HANA system has installed, the less possible security holes it might have)
For any server hardening, following procedure is used –
- Benchmark templates used for hardening
- Hardening parameters considered
- Steps followed for hardening
- Post-hardening test by DB/application team
The above procedures should help SAP customers in securing their servers (mostly on HP UNIX, SUSE Linux, RHEL or Wintel) from threats, known/unknown attacks and vulnerabilities. It also adds one more layer of security at the host level.
3. SAP Application (Transaction-level security)
SAP Security has always been a fine balancing act of protecting the SAP data and applications from unauthorized use and access and at the same time, allowing users to do the transactions they’re supposed to. A lot of thinking needs to go in designing the SAP authorization matrix taking into account the principle of segregation of duties. (SoD)
The Business Transaction Analysis (Transaction code STAD) delivers workload statistics across business transactions (that is, a user’s transaction that starts when a transaction is called (/n…) and that ends with an update call or when the user leaves the transaction) and jobs. STAD data can be used to monitor, analyse, audit and maintain the security against unauthorized transaction access.
4. SAP GRC
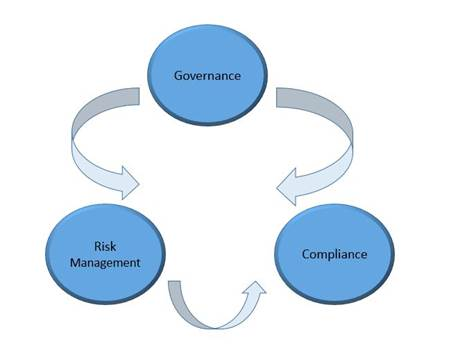
SAP GRC (Governance, Risk & Compliance) , a key offering from SAP has following sub-modules:
Access control
SAP GRC Access Control application enables reduction of access risk across the enterprise by helping prevent unauthorized access across SAP applications and achieving real-time visibility into access risk.
Process control –
SAP GRC Process Control is an application used to meet production business process and information technology (IT) control monitoring requirements, as well as to serve as an integrated, end-to-end internal control compliance management solution.
Risk Management
- Enterprise-wide risk management framework
- Key risk indicators, automate risk alerts from business applications
5. SAP Audit –
AIS (Audit Information System) –
AIS or Audit Information System is an in-built auditing tool in SAP that you can use to analyse security aspects of your SAP system in detail. AIS is designed for business audits and systems audits. It presents its information in the Audit Info Structure.
Besides this, there can be license audit by SAP and or by the auditing firm of your company (like Deloitte/PwC).
Basic Audit
Here the SAP auditors collaborate strongly with a given license compliance manager who is responsible for ensuring that the audit activities correspond with SAP’s procedure and directives. The number of basic audits undertaken is subject to SAP’s yearly planning, and it is worth noting that not all customers are audited annually.
The auditors perform below tasks (though they will vary a bit from organization to organization & from auditor to auditor):
- Analysis of the system landscape to make sure that all relevant systems (production and development) are measured.
- Technical verification of the USMM log files: correctness of the client, price list selection, user types, dialog users vs. technical users, background jobs, installed components, etc.
- Technical verification of the LAW: users’ combination and their count, etc.
- Analysis of engine measurement – verification of the SAP Notes
- Additional verification of expired users, multiple logons, late logons, workbench development activities, etc.
- Verification of Self Declaration Products, HANA measurement and Business Object.
SAP Enhanced Audit –
Enhanced audit is performed remotely and/or onsite and is addressed to selected customers. Besides the tasks undertaken in ‘Basic Audit’, it additionally covers –
- Checking interactions between SAP and non-SAP systems
- Data flow direction
- Details of how data is transferred between systems/users (EDI, iDoc, etc)
6. Security in SAP S/4 HANA and SAP BW/4 HANA
SAP S/4 HANA & SAP BW/4 HANA use the same security model as traditional ABAP applications. All the earlier explained components/security solutions are fully applicable in S/4 HANA as well as BW/4 HANA.
But these are increased security challenges posed by its component, SAP Fiori, which brings in mobility. But increased mobility means that data can be transferred over a 4G signal, which is not as secure and is easier to hack into. If a device falls into the wrong hands, due to theft or loss, that person could then gain unlawful access to your system. Its remediation is elaborated next.
7. Security in Fiori
While launching SAP Fiori app, the request is sent from the client to the ABAP front-end server by the SAP Fiori Launchpad via Web Dispatcher. ABAP front-end server authenticates the user when this request is sent. To authenticate the user, the ABAP front-end server uses the authentication and single sign-on (SSO) mechanisms provided by SAP NetWeaver.
Securing SAP Fiori system ensures that the information and processes support your business needs, are secured without any unauthorized access to critical information.
The biggest threat for an SAP app is the risk of an employee losing important data of customers. The good thing about mobile SAP is that most mobile devices are enabled with remote wipe capabilities. And many of the CRM- related functions that organizations are looking to use on mobile phones, are cloud-based, which means the confidential data does not reside on the device itself.
SAP Afaria, one of the most popular mobile SAP security providers, is used by many large organizations to enhance the security in Fiori. It helps to connect mobile devices such as smartphones and tablet computers. Afaria can automate electronic file distribution, file and directory management, notifications, and system registry management tasks. Critical security tasks include the regular backing up of data, installing patches and security updates, enforcing security policies and monitoring security violations or threats.
8. SAP Analytical Cloud (SAC)
SAP Analytics Cloud (or SAP Cloud for Analytics) is a software as a service (SaaS) business intelligence (BI) platform designed by SAP. Analytics Cloud is made specifically with the intent of providing all analytics capabilities to all users in one product.
Built natively on SAP HANA Cloud Platform (HCP), SAP Analytics Cloud allows data analysts and business decision makers to visualize, plan and make predictions all from one secure, cloud-based environment. With all the data sources and analytics functions in one product, Analytics Cloud users can work more efficiently. It is seamlessly integrated with Microsoft Office.
SAP Analytical Cloud use the same security model as traditional ABAP applications.
The concept of roles, users, teams, permissions and auditing activities are available to manage security.
9. Identity Management
SAP Identity Management is part of a comprehensive SAP security suite and covers the entire identity lifecycle and automation capabilities based on business processes.
It takes a holistic approach towards managing identities & permissions. It ensures that the right users have the right access to the right systems at the right the time. It thereby enables the efficient, secure and compliant execution of business processes.
10. IAG – (Identity Access Governance) for Cloud Security
SAP Identity Access Governance (IAG) is a multi-tenant solution built on top of SAP Business Technology Platform (BTP) and SAP’s proprietary HANA database. It is SAP’s latest innovation for Access Governance for Cloud.
It provides out of the box integration with SAP’s latest cloud applications such as SAP Ariba, SAP Successfactors, SAP S/4HANA Cloud, SAP Analytics Cloud and other cloud solutions with many more SAP and non-SAP integrations on the roadmap.
11. SAP Data Custodian
To allay the fears of data security in SAP systems hosted on Public Cloud, SAP introduced its latest solution called ‘SAP Data Custodian’. It is an innovative Governance, risk and compliance SaaS solution which can give your organization similar visibility and control of your data in the public cloud that was previously available only on-premise or in a private cloud.
- It allows you localize your data and to restrict access to your cloud resources and SAP applications based on user context including geo-location and citizenship
- Restricts access to your data, including access by employees of the cloud infrastructure provider
- Puts encryption key management control in your hands and provides an additional layer of data protection by segregating your keys from your business data
- Uses tokenization to secure sensitive database fields by replacing sensitive data with format-preserving randomly generated strings of characters or symbols, known as tokens
- With data discovery you can scan for sensitive data categories such as SSN / SIN, national ID number, passport number, IBAN, credit card, email address, ethnicity, et cetera, based on pattern determination and machine learning
12. Futuristic approach towards securing ERP systems
Driven by the digital transformation of businesses and its demand for flexible computing resources, the cloud has become the prevalent deployment model for enterprise services and applications introducing complex stakeholder relations and extended attack surfaces.
Mobility (access from smart phones/tablets) & IOT (Internet of things) brought in new challenges of scale (“billions of devises”) and required to cope with their limited computational and storage capabilities asking for the design of specific light-weight security protocols. Sensor integration offered new opportunities for application scenarios, for instance, in distributed supply chains.
Increased capabilities of sensors and gateways now allow to move business logic to the edge, removing the backend bottleneck for performance.
SAP has been investing a lot in drawing, refining its roadmap for security for the future.
It used McKinsey’s 7S strategy concept to review SAP Security Research and adapt supporting factors. Secondly, it assessed technology trends provided by Gartner, Forrester, IDC and others to look into probable security challenges.
As per SAP’s research, today’s big challenges in cybersecurity emanate around ML (Machine Learning). The trend is ML anywhere! ML itself provides a new attack vector which needs to be secured. In addition, ML is used by attackers and so needs to be used by us to better defend our solutions.
Machine Learning that has the most significant impact on the security and privacy roadmap these days, both providing the power of data to design novel security mechanisms as well as requiring new security and privacy paradigms to counter Machine Learning specific threats.
Deceptive applications is another trend SAP foresees. Applications must be enabled to identify attackers and defend themselves.
Thirdly, still underestimated, SAP foresees the attacks via Open Source or Third-party software. SAP has been adapting its strategy accordingly to tackle those new trends.
Wishing all SAP Customers a Happy, Safe and Compliant SAP experience!



















































